Attackers often use emails to gain initial access to a company. They do this by attaching malicious attachments or links to the emails, ultimately placing malware on the victim’s system.
Recipients are usually pressured into opening such malicious attachments or clicking on links, which causes the malware to be downloaded from the Internet and executed.
For example, attackers often carry out email spam campaigns containing invoices, payment notifications, invitations, etc. These are usually accompanied by Microsoft Office documents with macros attached or links, which are then used to install malware on the recipient’s computer.

Since most email services block executable attachments (.exe files), attackers often send them in container files such as .iso, .rar, and .zip. This allows the executable attachment to bypass the security gateways of the email service in question and reach the intended recipient.
This approach is demonstrated in this article by analyzing an email Oneconsult’s CSIRT received in March 2022, which contained an .exe file inside a .daa (Direct Access Archive) file. The email is shown below (see Figure 1). The .daa format is a proprietary file format developed by PowerISO for disk image files (see wikipedia). However, it is not natively recognized by Windows. Only Windows machines with such image editing programs already installed can open these files.
It is, therefore, important that such malicious email attachments are detected in good time and intercepted before they reach the recipient.
Caution! The following activities should always be performed in an isolated environment (e.g. virtual machine without network access). When analyzing malicious attachments, there is a risk of compromising the surrounding system.

How Can I Easily Detect a Malicious Email?
First, pay attention to the subject and the sender. If the subject does not seem relevant and the sender is unknown, this can already provide the first indication that this is not a legitimate email. Another indicator, which also applies to this example, is often the language – in this case, Spanish. This is even more true if such an email is not expected. It is best to delete the email directly to avoid any risk.
After that, a comparison of the email addresses can reveal inconsistencies. In this example, the email address in the signature (ecedillo[@]latco[.]com[.]mx) is not the same as the e-mail address of the sender (krane[@]kinesisindustryplc[.]us) (see Figure 1).
Furthermore, analyzing email headers can provide additional information. The headers contain important details such as information about the sender, recipient, subject, and date. The body of the email, on the other hand, contains the actual content. Some headers are hidden by email services, but they can be easily viewed by accessing the email’s properties in Microsoft Outlook, for example. An excerpt from the headers of the sample email is shown below (see Excerpt 1).
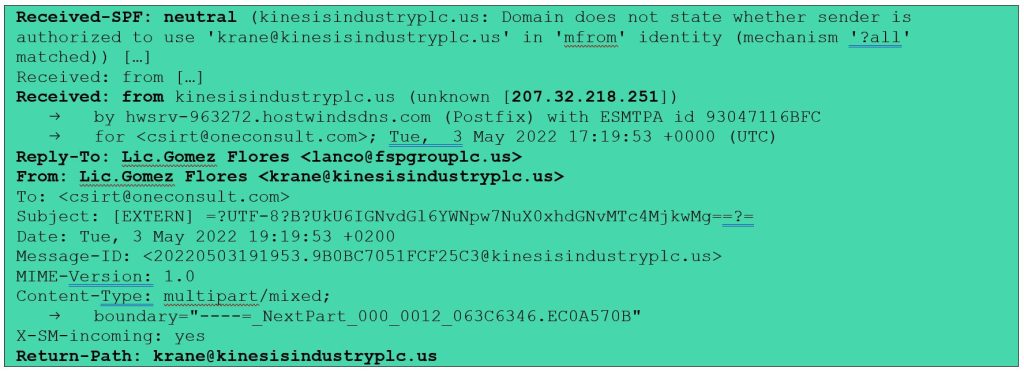
There are two email addresses in the headers: the sender’s (krane[@]kinesisindustryplc[.]us) in the “From” and “Return-Path” fields, and another in the “Reply-To” field (lanco[@]fspgrouplc[.]us) that has the same name as the sender (“Lic.Gomez Flores”) (see Excerpt 1). This is another inconsistency that raises a red flag.
Next, using online services such as VirusTotal, the reputation of the email addresses’ domains can be checked, i.e., whether they are known for malicious activity. In this case, at the time of writing, they are not known for such activities (see VirusTotal latco.com.mx, VirusTotal kinesisindustryplc.us, VirusTotal fspgrouplc.us). However, they are associated with emails detected by antivirus and security solutions that have a subject similar to our example, e.g., “FW cotización.msg” (see VirusTotal).
The “Received: from” fields provide details of the email’s transmission path, which can be used to determine which IP address the email was sent from. A search using an online service such as AbuseIPDB revealed that the specified IP address 207[.]32[.]218[.]251 (see Excerpt 1) is not especially known for malicious activity (see AbuseIPDB). However, it does not belong to the organization that sent the email, but to “1GServers LLC”, a web hosting service.
Another header that provides additional information for analysis is “Received-SPF”. SPF (Sender Policy Framework) is an email security protocol used to verify the sender. In our example, the code used is “neutral” (see Excerpt 1). This means that it does not specify whether the sender domain is allowed to use the email address entered. In phishing emails, it is common for the SPF code to be “fail” or “softfail”, indicating that the source IP is not valid for this email domain.
Finally, the content of the email shows further indications that it is a potentially malicious email. In this example (see Figure 1), the text urges you to open the attachment, as it states in capital letters and red font that a cost estimate should be prepared according to the attached technical specifications (“POR FAVOR COTIZAR DE ACUERDO A LAS ESPECIFICACIONES TECNICAS ADJUNTAS.”). The other part in capital letters indicates the verification of costs (“*VERIFICAR COSTO*”). Such spelling creates urgency and is intended to pressure the recipient, which is typical of malicious emails. In addition, there is no personal greeting, only a “Dear Supplier” (“Estimado Proveedor”). Other common clues would be language errors or an incorrect physical address or company.
Therefore, all the information gathered during the analysis indicates that this is most likely a malicious email.
How do I Find Out if the Attachment is Harmful?
A check of the attachment’s hash on an online service such as VirusTotal shows that it is a potentially malicious file. 23 out of 61 antivirus and security solutions detect the file as a Trojan.
If the file to be analyzed is not known by VirusTotal, an automatic dynamic analysis can be performed in an online malware sandbox. In this example, VirusTotal references an analysis of the “Hatching Triage” sandbox (see Triage). This revealed that the file “cotización_1782902.daa” contains the file “cotización_1782902.exe”, which has been identified as the malware “Xloader”.
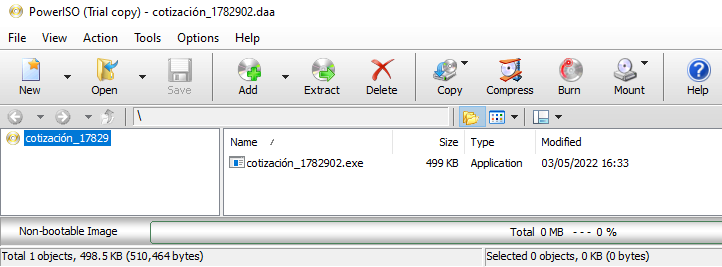
Another possibility is to perform a static analysis on a virtual machine. In this case, the file “cotización_1782902.exe” was extracted using the test version 8.2 of PowerISO (see Figure 2).
The executable file’s hash can be calculated and checked on VirusTotal, where 49 out of 69 antivirus and security solutions detected it as a “Trojan.” This demonstrates that using container files to package executables is highly effective, as the detection rate is significantly lower.
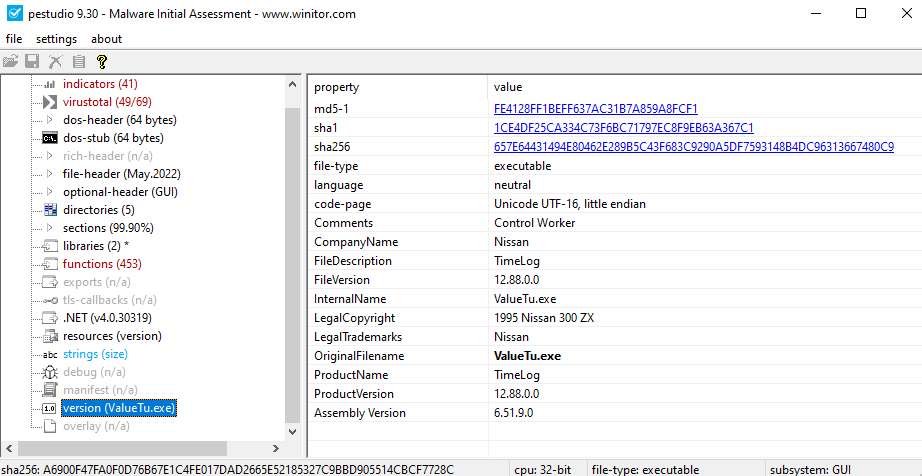
The .exe file can also be analyzed using a tool such as pestudio from Winitor . This tool can quickly find artifacts to provide an initial assessment of the malware. In this example, pestudio finds numerous artifacts indicative of malware. For example, strings and functions contained in blacklists such as “AsyncCallback” and “MD5CryptoServiceProvider” were identified. In particular, the analysis shows that the original file is named “ValueTu.exe” (see Figure 3).
The executable can also be dynamically analyzed using a malware sandbox. In our case, JoeSandbox identified “cotización_1782902.exe” as the malware “FormBook” through Yara rules (see Figure 4). FormBook is an alternative name for Xloader.
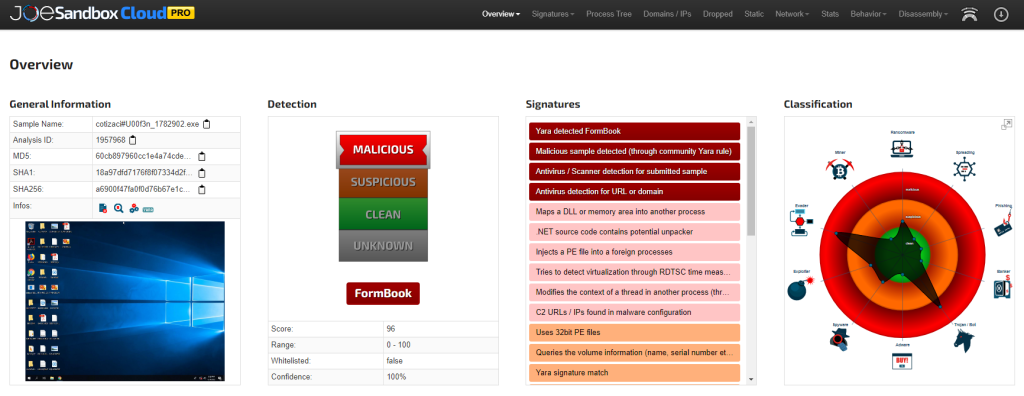
In the graphic (see Figure 4) on the right-hand side, the file is shown to have the characteristics of a “Trojan/Bot” and an “Evader”. This means that it can take control of the affected system to steal data such as credentials, log keystrokes, take screenshots, and so on. Additionally, it uses techniques to avoid detection, such as infiltrating other processes.
The analysis of the attachment thus indicates that it is a malicious attachment, as already suspected based off the email analysis.
Conclusion
Attackers often use container files to bypass security measures and distribute their malware via email. Inconsistencies in email addresses or signs of urgency and pressure in the email give additional clues that it is probably a malicious email. When it comes to attachments, a hash check with VirusTotal helps to quickly determine if it is malware. An automatic sandbox analysis, which can be conducted using a tool like pestudio, can provide additional insights if there is uncertainty.
In general, it is strongly recommended to train employees in the handling of emails, as they are the first line of defense against this type of attack. Unsolicited or unexpected emails should always be treated with suspicion. Employees should be made aware that they should not click on links or open attachments, especially if the email requests action and threatens consequences. In addition, it is advisable to block the receipt of dangerous email attachments at the email gateway, including .daa, .iso, .rar and .zip files. A more detailed list of file extensions to block is provided by GovCERT. Furthermore, if possible, attachments should be virus scanned at the email gateway and emails with positive results should be blocked.
Do you still have questions or would like our support? We look forward to hearing from you!




