Over the past few years, ransomware has become a serious threat to businesses that can cause significant damage. The financial impact of ransomware attacks is enormous – in addition to the cost of business interruption, organizations that fall victim to such an attack must also pay for the analysis and recovery of affected systems and data, as well as, in some cases, ransom demands.
A report published by the IC3 (Federal Bureau of Investigation – Internet Crime Complaint Center) in 2023 estimated the costs caused by ransomware in the US alone at over 60 million dollars. However, this figure reflects only a small part of the true costs. In addition to the financial loss, businesses must also reckon with reputational damage and a loss of trust among stakeholders such as employees, customers and suppliers.
In order to avoid this kind of serious damage and to provide the best possible protection against ransomware attacks, preventive measures are essential. This article provides an overview of the most effective steps you should take to protect your company against ransomware.
Table of contents
11 Measures to Protect Against Ransomware
In the following sections, key strategies for preventing a ransomware attack are outlined. From technical precautions to organizational measures – here you will learn how to increase the security level of your company.
The strategies described below are based on the recommendations of New Zealand’s Computer Emergency Response Team (CERT-NZ, see Figure 1) and the German Federal Office for Information Security (BSI).
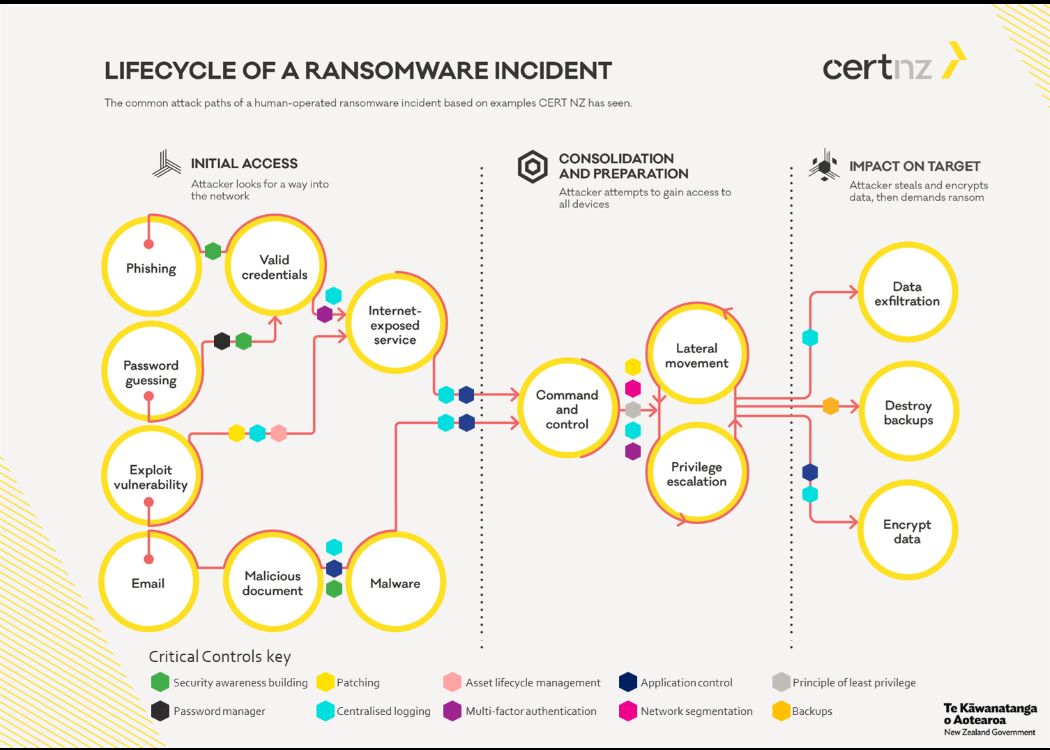
Unfortunately, there is no silver bullet against ransomware. Rather, it takes a combination of measures to effectively protect yourself. This combination minimizes the risk of an attack while at the same time creating hurdles that potential attackers will have to overcome first.
Closing Typical Entry Points for Ransomware
One important measure for preventing ransomware attacks is to close common entry points. This makes it much more difficult for potential attackers to gain initial access to their victim’s network. Relevant measures are described below. For a detailed description of the relevant attack vectors, see the blog article “Ransomware: Detection and Prevention“.
1. Patches and Updates – Keeping Systems Up to Date
To prevent vulnerabilities from being exploited, it is essential that all systems are kept up to date and patched regularly. If the use of legacy systems and/or software is unavoidable, it is recommended that they are separated from other systems and run in an isolated network zone. Implementing patch and vulnerability management is also advisable.
2. Securing Remote Access
Systems and services should not be exposed unnecessarily, as this increases the attack surface. Disabling ports and services that are not used is recommended. This is especially important for insecure and vulnerable services such as SMBv1 (Server Message Block). Organizations should also be aware of the services that are available on the internet. These can be identified by using external scans, for example with online services such as Shodan or Censys, or by using vulnerability scans. Once all services exposed to or accessible via the internet have been identified, multi-factor authentication (MFA) should be enforced. MFA is one of the simplest and most effective security controls to prevent unauthorized access.
3. Setting Up Secure Passwords and Multi-Factor Authentication
Strong authentication methods are required to protect your organization against phishing and brute-force/password spraying attacks. This includes implementing a password policy that makes it much harder for attackers to guess passwords. A very important factor here is password length. In addition, the “Local Administrator Password Solution” (LAPS) can be used to manage passwords for local administrators via Active Directory. Also, regular password audits are a good way to check the quality of passwords.
In addition to strong passwords, multi-factor authentication (MFA) should be implemented to provide a higher level of protection. Once MFA is set up, a user must authenticate with a second factor, such as confirming a push notification on their smartphone, in addition to entering their login credentials when logging in to their user account. Should attackers gain access to a valid password, for example through phishing, MFA prevents them from using it to gain unauthorized access to the associated account.
4. Increasing Email Security
There are several technical measures to protect against phishing and malspam. One such measure is to block certain attachments at the email gateway. Various blocklists are available for this purpose, for example those provided by GovCERT and Microsoft. It is recommended that attachments are scanned for viruses at the email gateway and that suspicious emails are blocked. In addition to that, SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance) should be configured to protect the email domain and prevent fake emails. An Email Security Assessment can help to review relevant configurations and settings.
5. Improving Cybersecurity Awareness
Humans should not be seen as the weakest link, but as the last line of defense against social engineering attacks such as phishing. By the time a phishing email reaches an employee’s inbox, technical defenses have failed. It is therefore important to build a well-informed and vigilant team of employees. Regular training on how to deal with emails and other cybersecurity issues is a must. Employees should be aware of the latest ransomware threats and phishing attacks and know secure online practices so they can recognize and report attacks. The IT and/or security team needs in-depth ransomware training to be able to respond quickly and effectively in an emergency.
Detecting and Blocking Cyberattacks
Throughout the course of a ransomware attack, it is crucial to detect and block the attackers’ activities – the earlier, the better. This is the only way to minimize the damage. Measures to help detect and block attacks are described below.
6. Actively Monitoring and Evaluating Alerts
Network visibility is critical for early detection of attacks. Therefore, steps should be taken to identify and prevent suspicious activity. To detect anomalous behavior and potential signs of ransomware activity early, implementing real-time monitoring solutions is recommended, such as antivirus, endpoint detection and response (EDR), canarytokens, and honeypots. Some of these solutions can automatically block an attack and/or take immediate action. Active monitoring also enables rapid response and containment, minimizing the impact of an attack.
Personnel are required to monitor and process the alerts generated by those tools. It is important that the responsible employees are able to distinguish between serious warnings and false alarms. The Antivirus Event Analysis Cheat Sheet by Florian Roth is a valuable tool to help you with this. However, the typically high number of alerts can also lead to analyst overload, which is known as alert fatigue. For countermeasures, see our blog article Alert Fatigue – Risks and Measures.
7. Setting Up Centralized Logging
To ensure a complete overview of events in your environment, it is essential to collect and store all logs centrally. This also makes it easier to reconstruct incidents. Relevant logs and events should be enabled (see, for example, the recommendations from Malware Archaeology). Since it is impossible to manually process all of this data, centralized logging is important. It must be ensured that all systems are in sync and use the same time source and time zone to facilitate event analysis and correlation.
In addition, the logs should be protected from modification and deletion. They should also be stored for an extended period of time, as incidents are often only discovered months after the first activities related to the incident have begun. In order to allow for an effective incident investigation, the logs should be available for a reasonable period of time. Alerts for known malicious or unusual events can also be configured to trigger notifications. Again, active monitoring and evaluation of events is required to respond quickly and effectively.
Preventing Ransomware Groups From Spreading
Ransomware groups often attempt to gain high privileges and spread across the network to cause the most damage. However, this is where you can make things difficult for the attackers. Some groups may give up when they realize that infiltrating the network requires too much effort. Instead, they will focus on a hit-and-run strategy, encrypting as much data as possible in a short period of time to maximize the number of victims. In such cases, network segmentation and the implementation of the “principle of least privilege” – that is, giving users only the permissions they need to do their jobs – are critical to limiting the damage.
8. Implementing Network Segmentation
Network segmentation divides a network into multiple zones or segments. This can be done both physically, using firewalls, and logically, using virtual local area networks (VLANs). For example, segments are created based on the criticality of systems and data. When doing so, it is important to ensure that only the required connections (ports and protocols) are allowed between zones, while all others are blocked. For sensitive segments, MFA and user-based access policies are essential. Network connections should also follow the principle of least privilege. Network segmentation also provides greater visibility because all communication between zones can be logged and monitored, which makes it easier to detect suspicious activity.
Without network segmentation, an attacker can spread through the network unhindered. Therefore, it is advisable to set up a separate network segment at least for critical systems and sensitive data. This isolates them and makes it more difficult or impossible for ransomware to spread within the infrastructure (so-called “lateral movement”), which reduces the risk of the entire network being compromised in the event of an attack.
9. Administrator Accounts – Integrating the Principle of Least Privilege
As mentioned above, access rights should be assigned according to the principle of least privilege, which means that users are granted only the access or permissions they need to complete their tasks. This limits an attacker’s options when an account is compromised and prevents users from installing or running unwanted software.
It is important to make sure that only a limited number of users have administrative privileges. In addition, service accounts should only have higher privileges if required. To implement this, appropriate policies can be used.
Furthermore, access rights should be regularly checked and monitored in order to detect any anomalies. Logging of activities performed by accounts with administrative privileges should be enabled to detect unexpected activities, such as changes at unusual times of day or activation of disabled accounts.
Minimizing Damage From Ransomware
If an attacker manages to infiltrate the network despite all these measures, it is still possible to mitigate the damage. To do this, it is necessary to develop an effective emergency plan in advance that can be followed in the event of a ransomware attack. Furthermore, regular backups must be created that can be successfully restored.
10. Ready for Emergencies – Preparing an Incident Response Plan
To respond quickly and effectively to an incident, an Incident Response Plan (IRP) should be developed in advance and practiced regularly. The plan should outline a structured procedure for handling a cyber incident and describe the steps that should be taken before, during, and after a cyberattack to minimize potential damage. The plan should cover the following aspects:
- Definition of events by severity
- Evaluation and classification of events
- IT emergency organization with definition of roles and responsibilities and procedure for reporting
- Procedure and measures to handle the incident, from identification to recovery and improvement
- List of contacts
It is also strongly recommended that an offline copy of the Incident Response Plan be kept, e.g. a hard copy or a USB flash drive. Failing to do so may cause problems if the IRP is also encrypted during a ransomware attack.
The Incident Response Plan should also include a strategy for dealing with extortion, including how to handle ransom demands and disclosure of data. If the attackers are contacted, experts should be consulted.
Regularly practicing the IRP, for example in the form of tabletop exercises, is important to ensure that everyone involved knows and understands their responsibilities and tasks in the response process.
11. Creating and Testing Backups and Data Backup Concept
If backups are also affected by ransomware, it may be impossible to recover systems and data. Simple copies to NAS (Network Attached Storage) are not a secure backup, as this storage will also be affected in the event of a ransomware attack. In fact, backups are a popular target for attackers because they store all sensitive and important data centrally. Therefore, it is even more important to store backups offline to provide the best protection against ransomware incidents.
Backups should be created according to the 3-2-1-1 rule: three copies of the data on two different media, with one copy off-site and one offline. Backups should also be encrypted to ensure that only authorized persons can access them. It is necessary to make sure that the encryption key cannot be deleted or changed in any way.
Backups should be retained for a period of time appropriate to the organization’s risk profile and should include a version history. This ensures that a slightly older but clean backup can be used in the event of a compromise. In addition, the integrity of the backups should be regularly monitored and tested. It is also recommended to create a comprehensive backup policy that clearly defines the relevant procedures and processes.
It is equally important to test the functionality of the backups to evaluate the possibility of a restore and to determine the time required for the restore. To this end, it is advisable to perform a full system restore every few months. If it is successful, you are optimally prepared.
Conclusion
Ransomware attacks are becoming increasingly sophisticated and pose a serious threat to businesses. Effectively protecting against this growing threat requires a comprehensive defense strategy that includes both technical and organizational measures.
By implementing network segmentation, applying the principle of least privilege, and establishing a reliable backup strategy, organizations can significantly reduce the risk of a successful attack. Regular employee training, the use of strong authentication methods, and active network monitoring are also essential to detect and defend against potential attacks at an early stage.
The key to effective protection is the combination of preventive measures and a well-thought-out Incident Response Plan. A proactive approach is critical to protecting your business and increasing your cyber resilience.
So don’t wait until it’s too late – start now and implement the recommended strategies to be best prepared for threats. We are happy to assist you with implementation or any questions you may have.
Contact us today for professional help with implementing protection measures against ransomware!