There has been a dramatic increase in the number of cyberattacks in recent years, affecting both companies and private individuals alike. Phishing emails and other attacks have become more or less an everyday reality at work. Ransomware attacks have a particularly high potential to cause severe damage – which is why they receive a lot of media attention.
Table of contents
- What Are Cyberattacks and What Types Are There?
- Who Is Affected by Cyberattacks?
- Effective Protection Against Cyberattacks
- 1. Knowing Your IT Infrastructure
- 2. Implementing Patch and Vulnerability Management
- 3. Hardening Systems
- 4. Minimizing the Attack Surface
- 5. Implementing Network Segmentation
- 6. Using Strong Passwords
- 7. Implementing Two-Factor Authentication
- 8. Ensuring Active Monitoring and Response
- 9. Improving Logging
- 10. Promoting Cybersecurity Awareness – Raising Employee Awareness
- Cyberattacks and Trends
- What If There Is a Cyberattack After All?
- Conclusion
Various statistics confirm the increase in cyberattacks. The Swiss National Cyber Security Centre (NCSC), for example, publishes weekly reports on the number of incidents reported, demonstrating the extent of the threat.
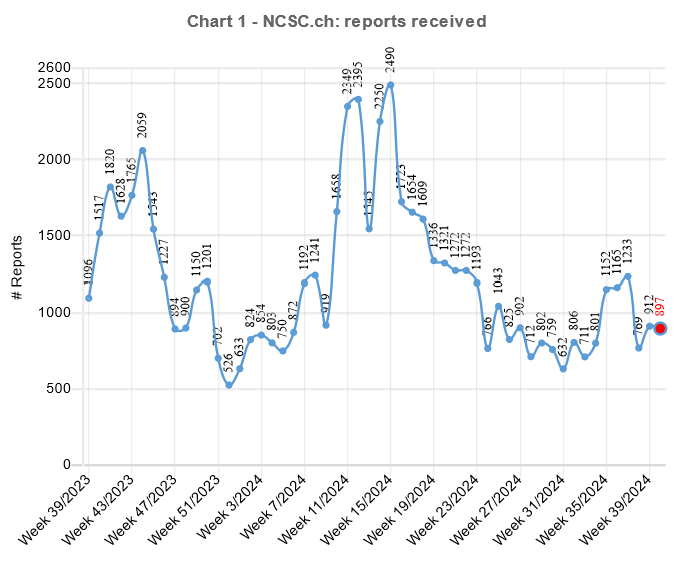
According to the NCSC semi-annual report for 2023/2, the number of cyber incidents reported to the NCSC almost doubled in the second half of 2023, compared to the same period in the previous year. While these figures give a good indication of the trend, the actual number is likely to be much higher as not all incidents are reported. The figures make it clear that cyberattacks pose a serious threat to businesses and that they should take immediate steps to protect themselves.
What Are Cyberattacks and What Types Are There?
Definition of Cyberattacks
The National Institute of Standards and Technology (NIST) defines a cyberattack as “any kind of malicious activity that attempts to collect, disrupt, deny, degrade, or destroy information system resources or the information itself”.
Who Are the Attackers and What Are Their Motives?
Cyberattacks are carried out by cybercriminals to infiltrate networks, compromise systems, disrupt services, commit financial fraud, and expose or steal intellectual property and other sensitive data. Attackers can be individuals or sophisticated groups that may be part of a criminal organization or state-coordinated. There are different types of attackers: script kiddies, cybercriminals, hacktivists, terrorists, insiders and advanced persistent threats (APTs), who have distinct levels of skills and resources. The motives also vary depending on the type of attacker. Possible motives include financial gain, political or geostrategic objectives, espionage, dissatisfaction and reputational damage.
What Are the Most Common Types of Cyberattacks?
Cyberattacks can take many forms and can be carried out in many different ways. The most common types of cyberattacks include:
- ransomware or malware
- social engineering attacks such as phishing, CEO fraud and other types of business email compromise
- DDoS attacks (distributed denial of service)
- botnets such as Mirai
Who Is Affected by Cyberattacks?
Cyberattacks can affect any organization, regardless of size or industry – cybercriminals target anyone. These kinds of attacks are common and also very present in the media. During the conference on peace in Ukraine, there were DDoS attacks in Switzerland against the websites of authorities and organizations involved in the conference. Not to forget the ransomware attack on Xplain last year. These examples are just a few of many similar incidents.
Since any company can become a target for attack, it is no longer a question of “if” but of “when”. The consequences of cyberattacks are wide-ranging: In addition to financial loss and disclosure of confidential information to third parties, there may be an interruption or impairment of business operations. In severe cases, this can even lead to a company going bankrupt. Other possible effects are reputational damage and psychological stress.
However, some organizations mistakenly believe that they are not a worthwhile target for cybercriminals and that there is nothing they can do to stop hackers. As a result, they do not take any measures to protect their infrastructure and also often do not have the budget to protect themselves in the best possible way.
But even if you only have a limited budget to spend on cybersecurity, there are still solutions available to help protect you from cyberthreats. The simplest and most effective protective measures against cyberattacks are described below, ranging from technical to organizational measures. For more specific measures to protect against ransomware, see the blog article “How To Protect Against Ransomware: Effective Tips for Companies”.
Effective Protection Against Cyberattacks
Under the “assume breach” approach, both preventative and reactive measures need to be considered. Adopting an “assume breach“ mindset means that it is assumed that a successful attack will occur at some point and therefore a worst-case scenario should always be expected. That is why it is important to create as many obstacles as possible for cybercriminals and to be prepared to detect and defend against attempted attacks as quickly as possible.
Most cyberattacks can be prevented by implementing effective protective measures. The effectiveness of the protection increases with each additional measure, as hackers have more obstacles to overcome or circumvent. This principle is known as “defense in depth“.
Such protective measures include organizational measures, like training and awareness-raising for employees, as well as technical measures, such as the use of strong passwords combined with multi-factor authentication (MFA), monitoring and vulnerability scans. Taken together, these measures help to reduce the risk of cyberattacks and achieve a high level of cyber resilience.
1. Knowing Your IT Infrastructure
Understanding, knowing and documenting your environment is essential to ensuring comprehensive protection.
Maintaining an inventory of the various systems, applications and services and managing them throughout their lifecycle is an effective way to keep track of installed versions and the timing of system replacements. This way you always know exactly which version is installed on which system. Furthermore, it is recommended that assets be prioritized. This has proven to be extremely useful, especially during the rebuilding process. Integrating the supply chain into asset lifecycle management is critical; suppliers and service providers must not be neglected.
Unfortunately, in a large number of incidents handled by Oneconsult, it has been found that many companies do not even keep a list of their systems and the IP addresses associated with them. It is equally important to have a network map that shows the different zones and systems in the network. This information is also extremely helpful in forensic analysis, particularly in understanding how the hackers moved through the network.
2. Implementing Patch and Vulnerability Management
A basic measure to protect against cyberattacks is to keep all systems up to date, as vulnerabilities that attackers actively exploit are constantly emerging. Prompt patching of vulnerabilities can close obvious gaps and attack vectors. Often, critical vulnerabilities in central applications, such as VPNs (Virtual Private Networks) or firewalls, are patched late or not at all, giving attackers the opportunity to use these vulnerabilities as entry points. This is why systems and services, especially those at the perimeter, must be updated regularly and promptly.
It is therefore highly recommended that you implement patch and vulnerability management. The US Cybersecurity & Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog provides an overview of the vulnerabilities that are actively exploited by cybercriminals. In addition, vulnerability scans should be performed on a regular basis to identify potential vulnerabilities and address them promptly.
3. Hardening Systems
Oneconsult’s experience has shown that systems are often not hardened in a proper or consistent manner. Basic protection of all systems is therefore another effective protective measure. A high level of cybersecurity can only be achieved by taking cybersecurity into account in the architecture and configuration of systems.
The blog article GPO Hardening: Most Important GPO Settings provides an overview of basic hardening measures for Active Directory. The CIS Benchmarks (Center for Internet Security) can be used for the further hardening of the systems in accordance with established standards. These benchmarks are pre-defined configuration recommendations for various products, not only for operating systems, but also for networking devices or the cloud, which should ideally be incorporated into a template.
4. Minimizing the Attack Surface
The attack surface describes all possible points at which a hacker could break into the environment. Minimizing the attack surface also reduces the number of potential entry points.
In general, only those services that absolutely need to be accessible from the internet should be accessible from the internet. Access to all other services, especially important, sensitive and vulnerable systems and services, should only be possible, for example, from behind a VPN secured by multi-factor authentication (MFA). Unfortunately, experience has shown that this is rarely the case.
In addition, regular scans should be carried out to check for external vulnerabilities and determine the extent to which your organization is vulnerable to attacks, for example by means of vulnerability scans or external services such as Shodan or Censys.
5. Implementing Network Segmentation
In a flat network, attackers can move freely and compromise all systems quickly and easily, which still happens all too often. This is why it is important to create a separate network segment for business-critical systems and data, which isolates and protects them. The risk of the entire network being compromised in the event of an attack on one segment is thus significantly reduced, which also helps to minimize the attack surface.
6. Using Strong Passwords
Using strong passwords is another preventive measure, which particularly helps to counter brute-force and similar attacks, in which passwords can be guessed or cracked. When handling incidents, Oneconsult still very often finds that weak passwords are used – even for administrator accounts, which could therefore be easily compromised. To learn how to create strong passwords, read the following article: Passwords: Common Mistakes, Best Practices & Tips. To enforce strong passwords, a password policy can be used. It is also recommended that you use a password manager to create and manage strong passwords. In addition, regular password audits can be performed to check password strength and determine if passwords have been compromised or leaked. Another useful tool is Have I Been Pwned?, which allows to check email addresses and passwords.
7. Implementing Two-Factor Authentication
Strong passwords will not protect you from phishing emails. If a password is revealed to an attacker, access to the account is possible, no matter how strong the password is. Enabling two-factor authentication (2FA) can help here. It can be implemented using an application or a physical key such as a FIDO2 YubiKey. 2FA prevents access to an account using only the password, thereby helping to prevent account compromise. However, it should be noted that 2FA alone does not provide comprehensive protection.
8. Ensuring Active Monitoring and Response
Central solutions such as antivirus, EDR (Endpoint Detection and Response) or NDR (Network Detection and Response) solutions help to detect threats by continuously monitoring systems and/or the network. They generate a variety of alerts to help identify and mitigate cyberthreats. Also, they can automatically stop attacks and initiate emergency measures such as isolating systems or blocking accounts.
It is recommended to review and test the extent to which the protection solutions in place are able to detect threats. The MITRE ATT&CK® Framework is a valuable tool in this regard, as it covers most of the tactics and techniques used by advanced persistent threats (APTs). It is important to ensure that the tools used have good detection width and depth, which means that as many tactics and techniques as possible should be covered. The matrix in figure 2 provides a comprehensive overview of the relevant tactics and techniques. For further information, see the blog article about Vulnerability Analysis With MITRE ATT&CK.
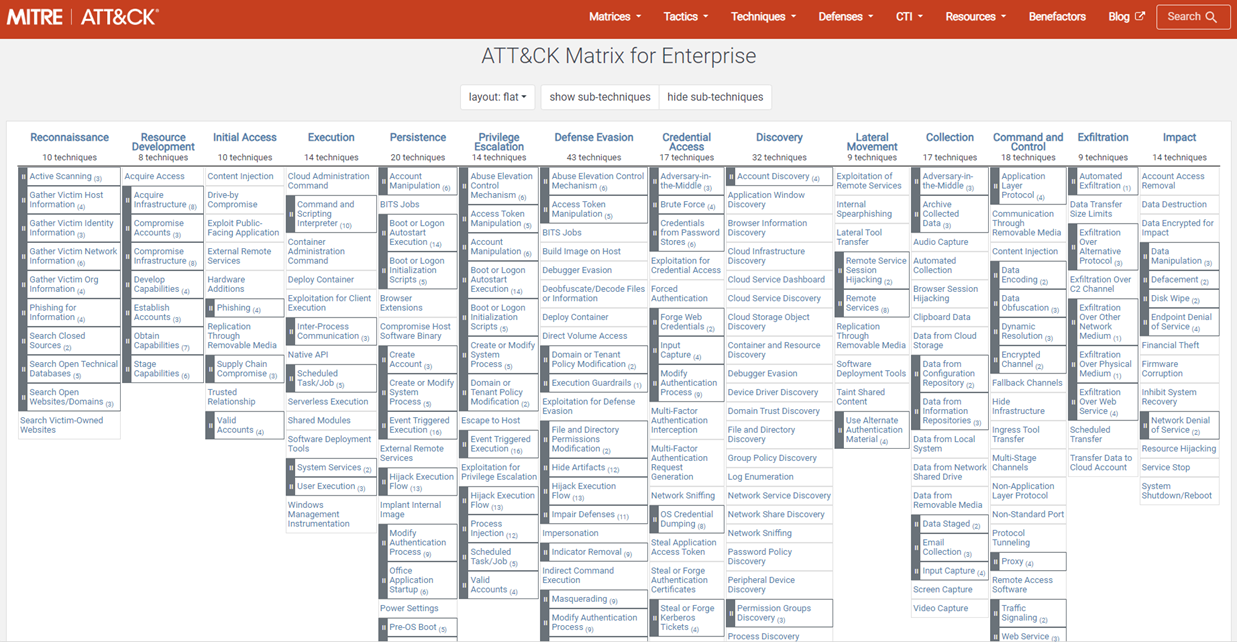
However, the security team in charge must review and promptly respond to alerts generated by the implemented protection solutions. If this is not the case, it is practically the same as not having a protection solution at all. To minimize the damage from cyberattacks, early detection through active monitoring and rapid response are critical.
9. Improving Logging
It is recommended that the logging process be improved and a logging concept developed, in addition to the measures already mentioned. The aim is to collect data relevant to the detection of known and common attack scenarios. In this way, attempted and ongoing attacks can be actively monitored and then analyzed in detail. This also makes the analysts’ work considerably easier.
Cheat sheets, such as those provided by Malware Archaeology for Windows or the BSI for Windows 10 (available in German only), provide recommendations on how to configure and set up the logs, including size, events to enable, etc. Furthermore, some websites like What2Log offer the possibility to create scripts to enable the relevant logs, both for Windows and Linux. Tools such as Sysmon (System Monitor from Microsoft’s Sysinternals Suite) can be used to generate additional events. Since incidents often affect several systems, all logs should be stored centrally so that they can be correlated and evaluated. In addition, it is necessary to store the logs for an appropriate period of time in order to enable a later analysis.
10. Promoting Cybersecurity Awareness – Raising Employee Awareness
Cybersecurity is everyone’s business: Employees in particular play a vital role that should not be neglected. It is therefore important to provide employees with the appropriate tools to help them identify and avoid threats. Employees should also know how to react and whom to contact in the event of an attack. So it is imperative to raise awareness among employees and train them on cyberattacks and best practices. This includes, among other things, how to handle phishing emails, links and attachments, the right level of caution when downloading files and the use of strong passwords. This can be done in the form of awareness presentations, trainings or even escape rooms. Cybersecurity awareness should be promoted throughout the organization, i.e., at all hierarchical levels, including management. Members of management play a crucial role in the handling of incidents and need to be aware of this responsibility. Technical teams should participate in additional in-depth training to enhance their technical expertise so that they are able to respond to cyberattacks and take appropriate action.
Cyberattacks and Trends
None of the above measures can guarantee 100% protection against cyberattacks. There is always a risk of certain measures being circumvented. Below you can find some example scenarios:
- Zero-day vulnerabilities: Updating systems does not protect against zero-day vulnerabilities. These are vulnerabilities for which no patch is available yet, as was the case with Ivanti at the beginning of the year. Supply chain attacks, such as the one in March 2024 affecting XZ Utils in Linux, cannot be prevented either.
- MFA fatigue: Two-factor authentication can be bypassed by so-called MFA fatigue attacks, for example. In such an attack, the attacker keeps sending authentication requests to the victim until the victim’s vigilance drops and they finally confirm a request. This way, hackers can successfully compromise their victim’s account.
- Bypassing protection systems: Modern protection solutions do not provide comprehensive protection against cybercriminals. There are types of malware that are capable of disabling common protection solutions. One example is Trickbot, which can disable Microsoft Windows Defender, as almost all ransomware groups do these days. Other examples of defense evasion can be found in the MITRE ATT&CK Framework.
What If There Is a Cyberattack After All?
The above examples show that, despite preventive measures, there is no guarantee that cyberattacks can be prevented. Should a cyberattack be successful, a rapid response is crucial.
The immediate measures to be taken depend on the individual case and the severity of the cyber incident. In minor cases, it may be sufficient to reset the account password or reinstall the system. In a severe case, however, the following steps are necessary:
- Contacting relevant parties who can assist in managing the incident, in particular the incident response partner.
- Isolating systems: affected systems or systems that have already been compromised to stop the attack from spreading and data from being exfiltrated; important and sensitive systems such as backups to protect them
- Restricting communication to and from the internet as far as possible to cut off the attackers’ communication channels
- Performing antivirus scans on all devices to determine the extent of the attack
- Blocking known IOCs (Indicators of Compromise) to keep hackers out
- Securing systems and data relevant for forensic analysis to reconstruct the attack, identify further IOCs, and take protective measures
- etc.
Conclusion
Cyberattacks such as phishing, distributed denial of service (DDoS) and ransomware have increased significantly in recent years and can have profound consequences for businesses – from financial loss and reputational damage to existential threat.
Any company can become a target for cybercriminals. It is therefore essential to take effective protective measures to prevent cyberattacks or at least to limit the damage. However, there is not one single measure that can be taken to fend off any cyberattacks. What is needed is a combination of technical and organizational measures, which include regular system updates, network segmentation, but also organizational measures such as the development of a security strategy and raising employee awareness. If these protective measures fail and an attack is successful, a rapid response is required. Working with an incident response partner can help limit the damage and make the right decisions in an emergency.