Ransomware represents one of the most significant and pervasive cyberthreats today. What originated as a relatively rudimentary blackmail tool has evolved into a highly sophisticated and organized criminal industry. Businesses and private individuals worldwide are confronted with this growing threat due to its relentless and indiscriminate nature.
In Switzerland, well-known organizations such as Neue Zürcher Zeitung (NZZ), Xplain, MCH, and Stadler Rail have already been affected by such ransomware attacks. The Comparitech map illustrates the global dissemination of cyberattacks:
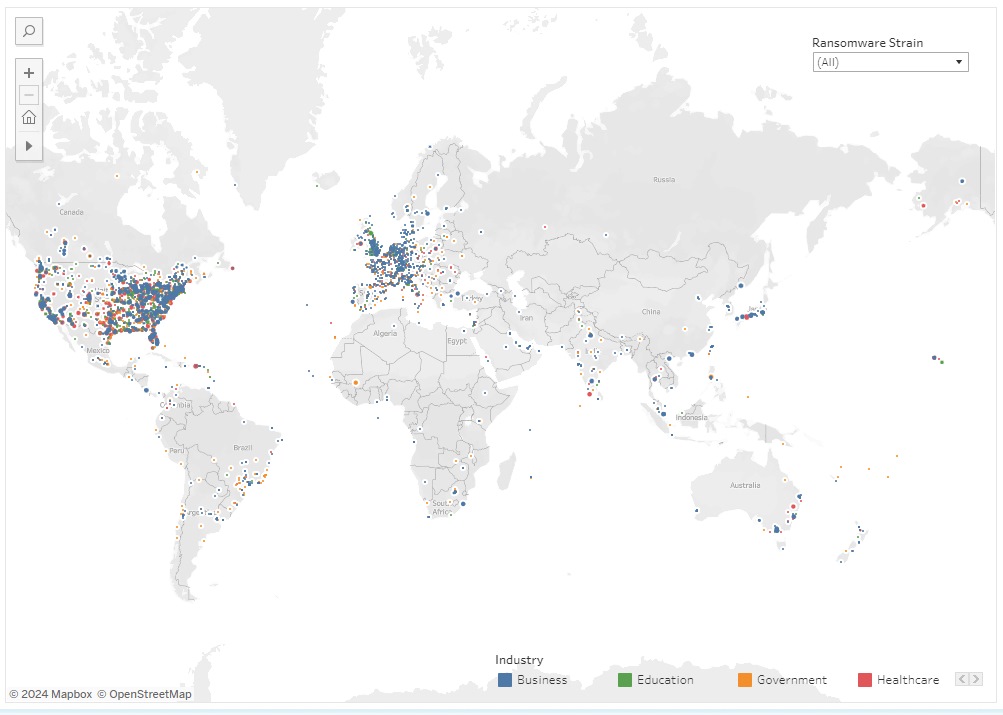
Other online services also document instances of ransomware attacks and those affected, providing interesting statistical insights. One such service is Ransom-DB, which illustrates the number of incidents/victims over time:
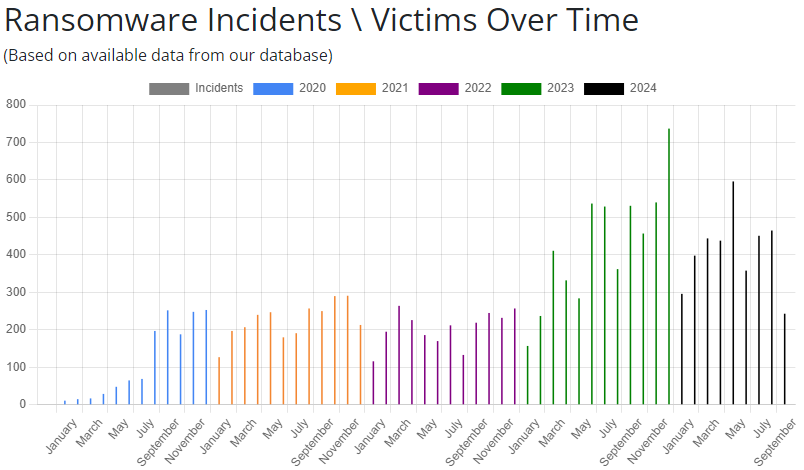
The data clearly demonstrates a notable increase in ransomware attacks in recent years. It is therefore important to have a clear understanding of what ransomware is and how such an attack works in order to be adequately prepared and to be able to respond effectively in the event of an incident.
Table of contents
Definition of Ransomware
The term “ransomware” is derived from the words “ransom” and “malware”. Ransomware is a type of malware that renders data inaccessible by encrypting it until a ransom is paid for the decryption tool. Should the ransom not be paid, the affected data can be made public. The ransom note is often stored on the affected system in the form of a text file and contains the amount demanded, the preferred payment method (usually in Bitcoin), payment instructions, and, in some cases, a specified deadline. It can therefore be concluded that ransomware is primarily used for financial motives.
Types of Ransomware
There are two main types of ransomware:
- Crypto ransomware encrypts the victim’s sensitive data, files, folders, and shared network storage. Doxware is a form of crypto ransomware that encrypts personal data and threatens to publish it – typically with the aim of intimidating or pressuring the victim into paying the ransom.
- Locker ransomware is a form of ransomware that locks the user out of the system. This means that the user’s screen is locked and they are unable to log in. A ransom note is displayed on the victim’s screen. This variant of ransomware usually does not use encryption.
Ransomware
The original intention of ransomware was to encrypt data or render it unusable and demand a ransom for its decryption. This type of attack persists to this day. They require relatively little effort from the attackers and can therefore be carried out on a large scale. The attackers are indifferent as to who the victim is, as evidenced by the numerous attacks on hospitals and other institutions.
Attacks often begin with the exploitation of readily exploitable vulnerabilities or scalable attacks using social engineering techniques, such as the dissemination of malspam (spam that contains malware) or phishing. Consequently, the automation of these attacks at the highest level is a relatively straightforward process.
Multi-Level Extortion
In response to the growing prevalence of ransomware, organizations have implemented a range of measures to enhance their cybersecurity. One notable strategy is the adoption of more robust backup procedures. This shift has made the traditional practice of encrypting data and subsequently extorting ransom payments a relatively ineffective approach, given that encrypted data can simply be restored from a backup.
In response, ransomware attackers have adjusted their strategies, resorting to the practice of stealing data before encrypting it and issuing threats to make it publicly available. This is often done by posting the data on a “data leak site” on the darknet. Such attacks are referred to as double extortion. This provides the attackers with further leverage in the ransom negotiations. Even if the victim is able to restore the files, the attacker still has the opportunity to make the sensitive data public if the ransom is not paid.
Some ransomware groups forego data encryption and instead focus exclusively on data theft and extortion. This is particularly prevalent in the cloud, where the nature of cloud technology makes it relatively simple for attackers to steal data, delete the original files, and then demand a ransom to restore and prevent the data from being published. For this reason, securing the cloud through penetration testing is recommended.
Triple or even quadruple extortion is also possible, where attackers additionally threaten the victim’s customers and other stakeholders with a Distributed Denial of Service (DDoS) attack and/or the release of data to exert further pressure.
Ransomware as a Service (RaaS)
Ransomware has evolved into a lucrative industry in its own right, known as “Ransomware as a Service” (RaaS) and referred to by Microsoft as “Human-Operated Ransomware.” This involves cybercriminals offering their ransomware to other hackers as a service. The attackers are now highly organized and structured, exhibiting a degree of professionalism. The RaaS model is based on the division of labor among different groups, which are designated as “Initial Access Brokers,” “RaaS Operators,” and “RaaS Affiliates,” as illustrated by Microsoft in Figure 3. Among the most prominent ransomware groups are LockBit, Conti, BlackCat, BlackBasta, Play, and Cl0p.
Initial Access Brokers specialize in unauthorized access to victims’ infrastructure and systems. Subsequently, the information is sold to RaaS Affiliates or other threat actors, who utilize it to facilitate their attacks.
RaaS Affiliates purchase or otherwise gain access to a victim’s environment and utilize the services provided by the RaaS Operators. The majority of the attack is carried out by them. The next steps are to move laterally, ensure persistence, steal data, and execute the ransomware. The technical expertise required to carry out these operations is minimal. The RaaS kits are designed for ease of use, with configuration and deployment requiring only a few clicks. The instructions provided by the RaaS Operators ensure a straightforward process.
RaaS Operators are responsible for developing the necessary tools, including the ransomware itself, operating the infrastructure, such as Command and Control (C2) channels, maintaining the data leak site, handling payments, and negotiating with victims. This streamlines the process, eliminating the need for many attackers or RaaS Affiliates to develop and program the ransomware themselves.
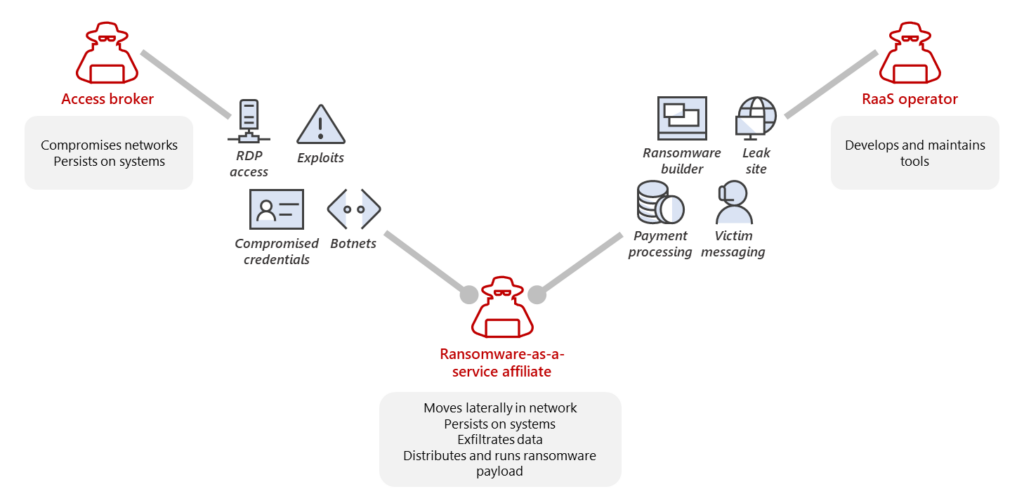
Ransomware attacks include automated processes for reconnaissance, such as vulnerability scans, initial access, such as phishing, and the distribution of the ransomware. The attackers are able to adapt flexibly to their victim’s environment by analyzing the organization in detail. This enables them to evade detection, inflict greater damage, and adjust the ransom demand based on the data obtained from the victim’s accounting system. However, despite their adaptability, it is important to note that ransomware attacks are ultimately executed by humans and remain susceptible to human error, which can be exploited to disrupt their activities or develop a decryption tool.
Who Is Most Susceptible?
Any company, regardless of its size or industry, is susceptible to a ransomware attack. Ransomware groups scan networks to identify potential security vulnerabilities they can exploit. Therefore, any device connected to the internet with inherent vulnerabilities should be regarded as a potential entry point.
The same principle applies to malspam. Ransomware groups disseminate their malicious email campaigns to as many potential victims as possible, and then await a response.
The time required for the reconnaissance phase varies between ransomware groups. Some groups conduct a more thorough analysis of the network before initiating an attack, while others employ a more opportunistic approach, targeting as many victims as possible with minimal effort. Regardless of the strategy employed, the objective is to maximize the number of victims and, consequently, the likelihood of a ransom payment.
The pertinent question, therefore, is not whether such an attack will occur, but rather when.
How Ransomware Works and How to Detect It
The progression of a ransomware attack typically encompasses several phases, as delineated by the New Zealand Computer Emergency Response Team (CERT-NZ) (see Figure 4). The specific tools and techniques employed by different attackers vary.
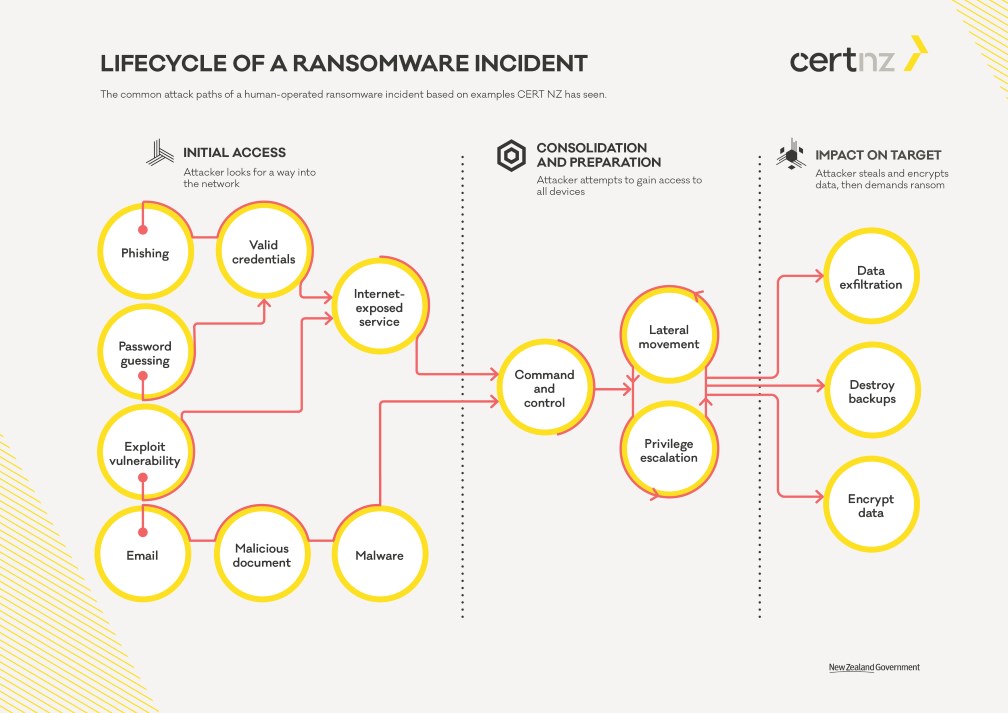
Phase 1 – Initial Access
The first step for any attacker is to gain access to the victim’s network. The most commonly used methods are brute-force or password-spraying attacks, social engineering attacks such as phishing, and the exploitation of vulnerabilities in exposed services. Further information on this topic can be found in the article “Cybersecurity: Guarding Against Unauthorized Access“. It is common practice for attackers to exploit vulnerabilities that are already known but not yet patched. For example, numerous vulnerabilities in VPN (Virtual Private Network) solutions, such as Cisco (CVE-2020-3259) and NetScaler (CVE-2023-4966), have been exploited by ransomware groups, including Akira and LockBit.
Phase 2 – Consolidation and Preparation
Once an attacker has gained access to a victim’s network, the next objective is to gain access to all relevant systems in the environment. To achieve this, the attacker will look for a way to gain domain administrator rights and access to critical systems such as domain controllers and backups. To do this, the attacker will need to spread further into the network using lateral movement.
Phase 3 – Impact on Target
In the final phase, the attackers collect and steal sensitive data. This is often done via the C2 channel or via services such as cloud storage or file-sharing solutions like Mega or Dropbox. To increase the pressure on the victim, backups are destroyed or deleted. Finally, the data and systems are encrypted, and a ransom is demanded to decrypt the systems and to keep the data confidential.
The so-called “dwell time,” i.e., the time between the initial intrusion and the discovery of the attack, has decreased in recent years: According to a study by Palo Alto Unit 42 Incident Response, it averaged at 13 days last year. Additionally, the time between the first compromise and the exfiltration of data has shortened to just two days.
At the same time, there has been an increase in the speed of encryption, although this varies depending on the type of ransomware. A study by Splunk shows that encrypting about 100,000 files (53 GB total) can take less than an hour in some cases. LockBit’s demonstrated exceptional speed, completing the encryption process in less than six minutes, making it the fastest ransomware in the study.
While ransomware attacks have become faster and more efficient, in some cases it can still be several months from initial access to encryption (Countdown to ransomware: Analysis of ransomware attack timelines). This is particularly the case with the RaaS model, where the initial access is gained before it is sold on to affiliates who then deploy the actual ransomware. The OCINT-CSIRT (Oneconsult International Computer Security and Incident Response Team) has already provided assistance in several ransomware incidents in which the initial compromise occurred more than six months prior. This allowed the attackers sufficient time to become familiar with the victim’s environment to cause as much damage as possible.
Should Ransom Demands Be Paid?
It is not recommended to pay a ransom in such circumstances. There is no guarantee that the attackers will fulfill their promise and actually decrypt the data or provide a decryption tool. There is also no way to ensure that the provided decryption keys are correct. Furthermore, despite all efforts, there is a possibility that the data could be published or resold.
It is not possible to guarantee that the attackers will cease their activities and leave the network. There is a possibility that the vulnerabilities discovered in the environment will be passed on to other criminal groups. It is therefore not possible to definitively exclude the possibility of a renewed attack on the organization.
Moreover, the act of paying the ransom serves to embolden the attackers, providing them with the financial resources to further develop their tools and methods, and to carry out additional attacks.
Should you still be considering making a payment, then it is imperative that you contact the relevant contact person / expert as soon as possible.
Immediate Measures in the Event of a Ransomware Attack
In the event of a ransomware attack, prompt action may still afford the opportunity to limit the damage. The following section presents a series of recommendations for responding to a ransomware attack.
Damage Control
Below is an overview of some of the best immediate steps you can take to limit the damage:
- Isolate Infected Systems by Disconnecting Them From the Network: Isolating an infected system cuts off communication with the attacker’s infrastructure and other systems, stopping the spread and the exfiltration of data. This can be done by simply unplugging the network cable or turning off the wireless adapter. Alternatively, isolation can be achieved with an Endpoint Detection & Response (EDR) solution. It is important to ensure that backups and other critical systems are protected, and to consider the impact on key systems such as the domain controller. Internet communication should also be kept to a minimum.
- Block Suspicious IP Addresses, Domains, and URLs on Perimeter Devices (Firewall, Proxy): Suspicious activity can be detected in the logs of the perimeter devices or the email server. Other Indicators of Compromise (IOCs), such as hashes of malicious files or malware, can be easily identified and blocked using protective software and systems (antivirus/EDR).
- Deactivate/Block Affected Accounts to Prevent Access by Attackers: In a ransomware attack, attackers often leave the ransom note in the form of a “read-me” text file. By reviewing the file properties of this file as well as the encrypted files, user accounts that may be associated with the creation of these files can be identified. This is an important indication of compromised user accounts.
- Reset All Passwords, Create Temporary Administrators, and Perform Continuous Monitoring: Resetting all passwords, including Kerberos passwords, is also highly recommended. It is important to ensure that you do not reset passwords that are required for recovery to avoid locking yourself out. It is also recommended to create temporary administrators for the recovery and to monitor the original accounts on an ongoing basis.
- Improve Visibility: The implementation of supplementary logging and monitoring procedures, along with additional sensors on systems and within the network, can facilitate continuous monitoring to detect and prevent malicious activity.
Escalation and Communication
It is also essential to implement immediate organizational measures:
- Comply With Reporting Procedures: It is crucial to inform certain groups of people promptly. This includes, for example, the incident response partner, who must be involved immediately. Furthermore, escalation within one’s own organization is necessary to ensure that all relevant individuals are informed and involved. This includes, among others, the management, data protection officers, and the legal department. Employees should also be informed in a timely manner, and communication with the public (media/press) should be prepared. In this regard, the recommendations of the CERT-NZ and the NCSC (National Cyber Security Centre) can serve as a valuable reference point. For more information on the necessary measures, please refer to the article “The 7 Red Flags When Creating an Incident Response Plan“.
- Check Reporting Obligations: Contracts with stakeholders such as customers, suppliers, insurers, etc. should be reviewed to determine if there is an obligation to report and what deadlines must be met. In some cases, depending on the infrastructure and country, it may also be necessary to report the incident to the relevant authorities, particularly in the event of a data breach, which is often the case with ransomware incidents.
- Decide How to Respond to Extortion and Ransom Demands: In the event of a ransomware incident, a prompt decision must be made regarding how to address the blackmail and ransom demands, as the attackers’ countdown is ticking. When making a decision, it is important to consider the availability of backups, and whether further information on the attack is necessary or if the priority is to simply buy as much time as possible. In the event that contact is initiated with the attackers or a ransom is being paid, it is imperative to seek the guidance of professional experts.
Analysis
An analysis of the attack should also be part of the immediate measures:
- Determine the Scope of the Attack: To determine the scope of the attack, antivirus scans are performed using existing protection software and systems (antivirus, EDR, etc.), as well as IOC scans using specialized tools (YARA, Thor Lite). Forensic tools such as Velociraptor can also be used to find and isolate already infected systems and block newly identified IOCs.
- Conduct Forensic Analysis to Reconstruct the Ransomware Attack: In the event of a ransomware attack, it is essential to conduct a forensic analysis to reconstruct the attack. This allows for a comprehensive understanding of the incident, from the initial breach to the exfiltration of data and the exact time of the attack. However, this process is contingent upon the availability of the necessary data. The analysis helps to detect further IOCs and also enables the identification of additional appropriate measures and the development of an effective recovery strategy. .
- Preserve Data for Forensic Analysis: Data required for a forensic analysis must be saved in a suitable manner. To this end, it is necessary to create snapshots of virtual machines and export logs from perimeter devices and servers. A triage of relevant systems, such as the domain controller, must then be conducted. Velociraptor can be utilized to facilitate this process. For guidance on data backup as well as the subsequent investigation, it is advisable to seek the expertise of professionals.
- Back up and Save Encrypted Data: Data that has already been encrypted should also be backed up and stored. If no decryption tool exists yet, it is possible that such a tool will be developed so that the data can be decrypted at a later date.
Recovery
Recovery measures are equally important:
- Choose an Appropriate Recovery Strategy: Especially in the case of a ransomware attack, it is often the case that all systems are affected and must therefore be restored from a backup or set up anew. However, this involves significant effort. It is thus crucial to select a suitable recovery strategy. If an error occurs, for example, because an infected system is overlooked or not properly cleaned, the entire recovery process must be restarted.
- Prioritization of Systems: The prioritization of systems is also of great importance for the facilitation of recovery. When restoring critical systems, it is of the utmost importance to consider potential dependencies and to restore the systems in the correct order. The recovery phase thus plays a significant role in the overall incident response process and has a substantial impact on the success of any measures taken to limit the damage and to recover the system.
- Prevent Reinfection With a Targeted Vulnerability Analysis: To prevent re-infection, a thorough forensic analysis is essential. This provides information about when and how the attackers penetrated the network, allowing the implementation of suitable measures to close the entry point. The analysis also helps to select the most appropriate backups for recovery. For instance, if the entry vector was the exploitation of a specific vulnerability, that vulnerability must be patched accordingly.
- Increase Resilience: As part of the recovery process, it is essential to implement measures that will enhance the organization’s resilience. These include, among other things, the introduction of a password policy, the use of Multi-Factor Authentication (MFA), and the implementation of hardening measures. The implementation of several measures as part of a defense-in-depth approach can help protect against ransomware like LockBit, thereby improving the company’s cyber resilience in the long term. Further preventive measures for protection against ransomware will be discussed in a future blog post.
Conclusion
Ransomware is a growing threat to businesses. The evolution of these attacks, especially with groups such as LockBit, and the move towards multi-level extortion or the professional Ransomware-as-a-Service model, highlights the importance of remaining vigilant and continually investing in your own cybersecurity.
Ultimately, it is the combination of technical preparedness, awareness of such attacks and a rapid, well-coordinated and professional response that makes all the difference when it comes to minimizing the impact of a ransomware attack.
If you do fall victim to a ransomware attack, you should contact an expert immediately to help you take the right steps to minimize the damage.
Want to learn more about ransomware and train your employees? Contact us for ransomware training or a ransomware awareness presentation.



