In an increasingly digitalized world, companies of all sizes and in all industries are at risk of cyberattacks. It is therefore crucial for businesses to prioritize network security in order to protect sensitive information and business processes. Every year, thousands of attacks on corporate networks are recorded, whether by hackers, insiders, or automated malware. The consequences of such attacks can be severe, including data loss, business interruptions, significant financial losses, and a loss of customer trust.
Organizations must take proactive measures to address these threats and ensure the security of their IT infrastructure. One of the most effective ways to find and fix network vulnerabilities before attackers can exploit them is to perform a network penetration test.
In this blog post, we will discuss how a network penetration test is conducted, what its objectives are, what tools and techniques are used, and what best practices organizations should follow to improve their network security and protect themselves against future threats.
Table of contents
What is a Network Penetration Test?
Network penetration testing, also known as a “pen test,” is a specific type of penetration testing that focuses on assessing a company’s entire computer network using ethical hacking techniques.
The primary objective of network penetration testing is to uncover and identify potential vulnerabilities within the organization. This involves a comprehensive evaluation of network security measures, including external and internal assessments such as web application testing and simulated phishing attacks.
How Does a Network Penetration Test Work?
A network penetration test, also known as a network security assessment, involves a series of steps designed to identify, analyze, and ultimately mitigate potential vulnerabilities in an IT infrastructure. From initial information gathering and detailed component analysis to follow-up and reporting, each step plays an important role in strengthening network security and recommending targeted measures to address vulnerabilities.
- Enumeration and Vulnerability Analysis: The first step is to gain a comprehensive understanding of the infrastructure. Penetration testers gather detailed information about the network, devices in use, IP addresses, applications, and more. They use security and vulnerability scans to scan the network for open ports, outdated software, or misconfigured services. These scans are particularly useful for identifying easy-to-exploit vulnerabilities, also often referred to as “low-hanging fruit”. Tools such as Nmap and Nessus are often used for this purpose.
- Pentest / Review / Audit: The subsequent step is a detailed analysis of the network, in which the individual components are examined in greater depth. The components to be analyzed can be determined in advance through collaborative planning or based on the results of the previously performed scans. Depending on this, the appropriate test type can then be selected. The different test types are explained in more detail below:
- System Penetration Test: The objective is not to take over the system, but to create a comprehensive list of all its vulnerabilities. Systems under analysis may include both external and internal components. The objective of a system penetration test is to evaluate the effectiveness of security measures implemented in both the vulnerable systems and those that have already been hardened.
- Firewall Security Assessment: A Pentest Firewall is ideal for environments where the infrastructure is protected by one or more firewalls. When securing multiple subnets or using multiple firewalls, the rulesets can quickly become complex and confusing. Even with an optimal set of rules, misconfigurations can occur within the firewall itself. A thorough firewall security assessment uncovers potential misconfigurations or vulnerable rulesets and helps to significantly reduce the attack surface.
- Wireless LAN Security Assessment (WLAN): WiFi networks offer a range of security standards and settings, with varying degrees of protection. Incorrect configuration can leave the network vulnerable to attack. Even with low-cost equipment, a WiFi signal can be received over long distances, enabling an attacker to access the WLAN without physical contact. This initial access could then be used for further attacks against internal systems. A comprehensive WLAN security assessment can identify misconfigurations, insecure settings, and inadequate security measures, leading to a substantial enhancement in network security standards.
- Email Security Assessment: Email servers are often exposed to the internet, making them a frequent target for attackers. Poorly configured email servers can be used to send spam or provide an entry point into the internal network. If an employee clicks on a malicious email attachment, an attacker can gain initial access to the internal network. An email security assessment helps identify misconfigurations of security settings and measures, and can show, for example, which email attachments were filtered and which were not. Based on these findings, the level of security can be improved.
- VPN Penetration Test: This type of test examines the Virtual Private Network (VPN) for vulnerabilities to ensure that external connections are properly secured against unauthorized access and data breaches.
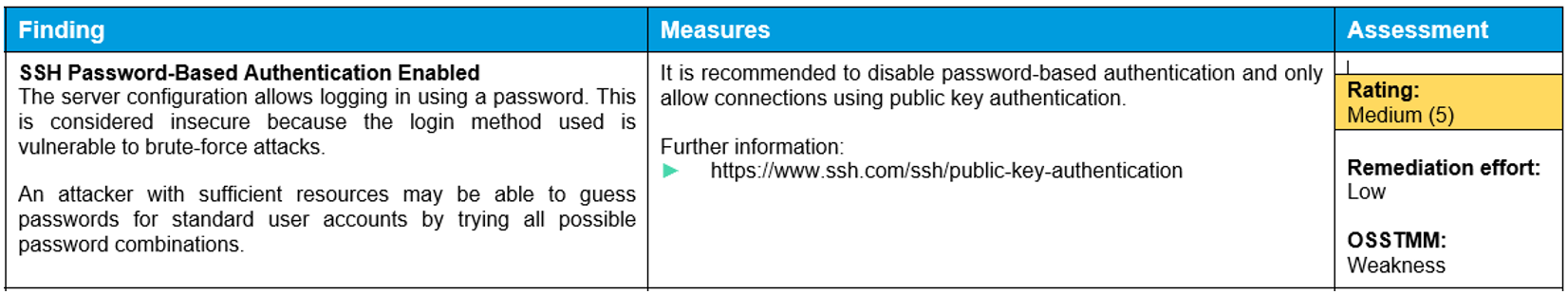
- Follow-Up and Reporting: Following the completion of testing, the penetration testers document the identified vulnerabilities (Findings) in detail and assess them based on their severity and likelihood (Assessment). The report also includes specific recommendations (Measures) on how to address the vulnerabilities to ensure long-term system security. The following example illustrates a finding from a final report by Oneconsult:
Objectives of a Network Penetration Test
A network penetration test has various objectives for improving the security of a network.
- Identifying Vulnerabilities: The objective of the penetration test is to identify potential security vulnerabilities before attackers can exploit them. This involves identifying entry points, such as open ports, and analyzing them for vulnerabilities, as well as detecting insecure configurations, outdated software, and weak passwords.
- Evaluating Risks: After identifying the vulnerabilities, they are evaluated according to their severity and the probability of a successful attack. In addition, a classification according to the OSSTMM Framework is carried out. These classifications help to prioritize the necessary measures.
- Meeting Compliance and Security Standards: Many companies are obligated to comply with legal or industry-specific security standards. Penetration tests verify and provide evidence of compliance with these standards.
- Providing Recommendations: Following testing, companies receive a detailed report with specific recommendations for addressing the identified vulnerabilities and improving their security posture.
Methods and Tools of a Network Penetration Test
Penetration testers use a variety of tools and methods to uncover vulnerabilities in networks. Generally, two approaches are distinguished:
- Automated: Tools are particularly useful for quickly and efficiently scanning large networks for vulnerabilities. They provide a comprehensive overview and enable the detection of known security gaps.
- Network scanning tools: These tools are used to detect devices, open ports, and running services in a network. They provide an initial overview of the network structure and identify potential attack points. Examples: Nmap, Zenmap.
- Vulnerability scanners: These tools scan systems for known vulnerabilities documented in databases such as “Common Vulnerabilities and Exposures” (CVE). They provide detailed information about the severity and exploitability of the vulnerabilities found. Examples: Nessus, OpenVAS.
- Manual: Manual tests require the expertise of a penetration tester and allow for a more in-depth analysis. They are particularly effective in uncovering complex vulnerabilities that automated tools cannot detect.
Best Practices and Recommendations
Conducting network penetration tests on a regular basis is a key component of a robust cyber defense strategy. To maximize the benefits of these tests, the following best practices should be followed:
- Regular Execution and Adaptation: Penetration tests should be carried out at regular intervals to keep pace with the constantly changing threat landscape. The frequency of the tests depends on the size of the company, the industry, and the complexity of the IT infrastructure.
- Objective and Definition of the Scope: Prior to conducting a test, it is essential to establish clear objectives and define the scope. This encompasses the systems to be assessed, the methods to be employed, and the anticipated outcomes.
- Combining Manual and Automated Testing: Manual and automated tests have their respective strengths. Manual tests allow for more in-depth analysis, while automated tests are suitable for quickly and comprehensively checking large networks.
- Deployment of Qualified Penetration Testers: The selection of experienced penetration testers is crucial to the success of a test. These experts have the necessary knowledge and skills to identify and target complex attack vectors.
- Detailed Documentation and Follow-Up: The results of a penetration test should be summarized in a detailed report. This report should contain all the vulnerabilities identified, their severity, and specific recommendations for action. The implementation of the recommendations should be regularly reviewed.
Furthermore, the following points should be implemented and adhered to by the company:
- Involvement of the Entire Company: Security measures are a collective responsibility. All employees should be sensitized to the topic of IT security and be aware of their role in defending against cyberattacks.
- Patch and Configuration Management: Effective patch management and consistent configuration of systems are crucial to address known vulnerabilities and ensure a uniform security level.
- Access Permissions and Role Concept: Access permissions should be limited to the necessary minimum to reduce the risk of data leaks. A clearly defined role concept facilitates the management of access permissions.
- Emergency Planning: An emergency plan should be created for the event of a successful attack. This plan should describe in detail the response to such an incident.
- Continuous Improvement: The results of penetration tests should be evaluated on an ongoing basis to further improve existing security measures.
How Can Oneconsult Assist?
Oneconsult’s Network and Security Infrastructure Tests provide valuable insights into the extent to which you have vulnerabilities under control and identify any existing security gaps. Our comprehensive assessments and analyses reveal potential security risks, vulnerabilities, and threats within your network and security infrastructure, enabling you to address these issues proactively before they can be exploited by cybercriminals.
In addition to network penetration testing, Oneconsult offers a diverse array of services designed to enhance your organization’s defenses against cyberthreats. Our team of qualified penetration testers is dedicated to helping you identify and remediate vulnerabilities while strengthening your overall security posture.
Conclusion
Network penetration tests are an essential security strategy for any company that wants to protect its digital assets and sensitive data. In an increasingly interconnected world, where new cyberthreats are constantly emerging, it is crucial to identify security vulnerabilities before they can be exploited by attackers. A penetration test offers a structured and targeted approach to test a company’s defense mechanisms and find potential weaknesses that might otherwise remain undetected.
By proactively identifying security gaps in the network infrastructure, attacks can be prevented before they occur. Penetration testers simulate real threats and attack vectors to gain a comprehensive picture of network security. This not only reduces the risk of data loss but also improves protection against financial damages that could result from attacks.
Overall, a network penetration test is more than just a one-time check of the network security – it is an indispensable component of a comprehensive security strategy that helps protect companies from current and future cyberthreats.




