Ransomware is currently what everybody is talking about. Everyone fears becoming a victim and bearing the consequences for their reputation as well as the financial impact of it.

The scam
The blackmailers send e-mails claiming that they have hacked the company’s website and stolen data that they will publish on leak websites, if the ransom is not paid. E-mails like this are sent by blackmailers en masse.
For companies, the main threat is that their data will be published after their website is compromised. They can only prevent this by paying a certain amount of Bitcoin.
Is this a serious statement or just a bluff? This article is about how to deal with and counteract extortionist scams.
Procedure – Analysing the E-Mail
The Oneconsult International Computer Security Incident Response Team (OCINT-CSIRT) was contacted by a company that had received such an extortion e-mail (see Figure 1). Allegedly, the company’s website had been hacked and they had to pay a ransom to prevent the publication of the stolen data.

The client asked us to analyze the e-mail to find out if and how to respond to it.
Quick & Dirty Search
Since the e-mail was not forwarded as an attachment, the e-mail header information was not available for analysis. In such a case, only a brief examination of the e-mail based on the information contained in the text is possible. So there is only the email address and the two parts of the bitcoin address (see red boxes on figure 1) of particular interest and great importance for the analysis.
First, the e-mail address in question was checked on several online services, including emailrep.io. This revealed that the e-mail address is undeliverable and, moreover, the associated domain has a negative reputation.
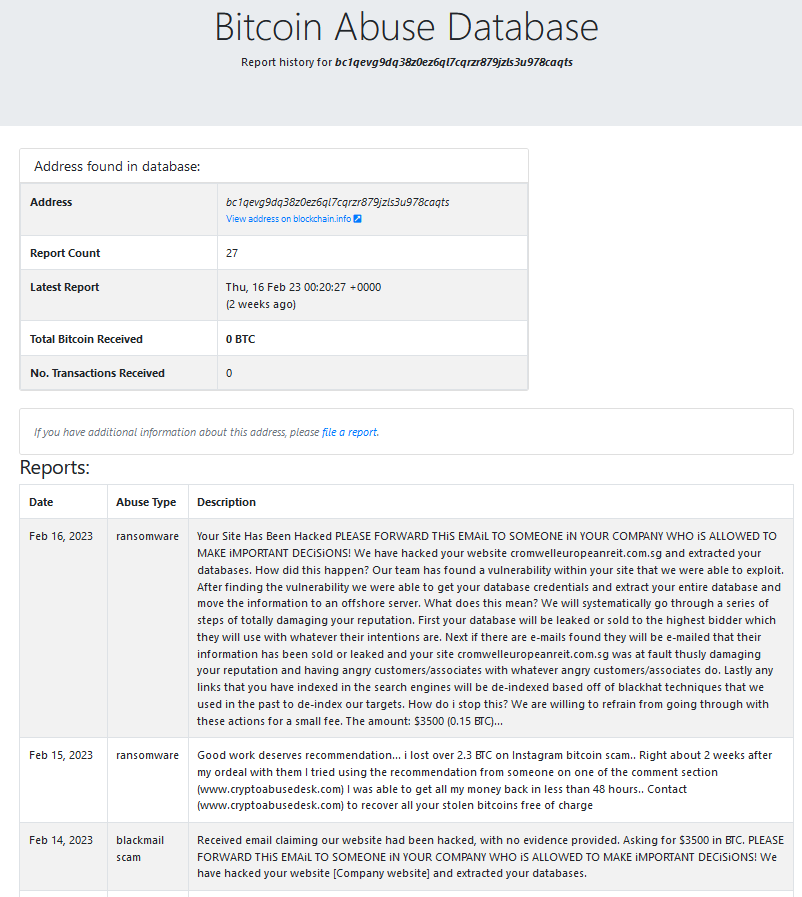
The Bitcoin address was then searched for on the website bitcoinabuse.com. As shown in Figure 2, it is clearly indicated that this was a scam. Additionally, it was found that the same text was reported multiple times in connection with this Bitcoin address (see Figure 1).
This quickly led to the conclusion that we are facing a scam attempt in this case.
Recommended Measures in Case of extortion E-Mails
Such emails are sent en masse in the hopes that one of the recipients will be intimidated into paying the ransom. It is recommended that you do not pay the ransom under any circumstances. If you already have, you can file a criminal complaint with the police. You should report the Bitcoin address to both the police and the Bitcoin Abuse platform so that they can trace the transactions on the attackers’ accounts.
Generally, such e-mails can be ignored and deleted. In case of doubt, you can get professional support from a Digital Forensics team. Moreover, you can have your website checked by an expert with a Penetration tests.
Conclusion
Overall, it is important to emphasize that extortion e-mails claiming to have hacked a company’s website and stolen data, can pose a serious threat. However, it is also important to note that many of these e-mails are fraudulent and do not indicate an actual compromise.
As an organization, you are advised to stay vigilant and watch for potential threats. If you have further questions about ransomware attacks or need assistance, you can contact us without any obligation:




