With the Digital Operational Resilience Act (DORA), the EU has created a sector-wide regulation regarding cybersecurity, ICT risks and digital operational resilience for the finance industry. It will come into force in January 2023 and must be complied with by January 17, 2025.
Table of contents
- Security Testing in Accordance with DORA
- Impact of DORA on Swiss Financial Entities and ICT Service Providers
- Threat-Led Penetration Testing (TLPT) in Accordance with DORA
- Testing of ICT Tools and Systems and TLPT by Oneconsult
- TLPT Procedure in Germany
- Does Oneconsult Fulfill the Requirements for TLPT According to DORA?
- Further Support From Oneconsult
- Conclusion
Security Testing in Accordance with DORA
In addition to other important points, tests of digital operational resilience (Articles 24 to 27) are relevant as essential elements for implementation. A distinction is made between two types of tests: “Testing of ICT tools and systems” and “Extended tests based on TLPT.” This article describes the requirements in connection with DORA in the EU area, with specific reference to the concretization by BaFin for Germany (German Financial Supervisory Authority). With regard to the topic of cyber resilience, Swiss financial entities are required to comply with a number of regulations, including those set forth by FINMA (Swiss Financial Market Supervisory Authority), which were communicated in Circular 2023/1, for example. However, it is important to note that they may also be affected by DORA.
Impact of DORA on Swiss Financial Entities and ICT Service Providers
DORA will also have an impact on financial entities and ICT service providers in Switzerland. Swiss financial entities may also be required to comply with obligations under DORA if they operate in the EU or maintain relationships with other financial entities or their customers in the EU. Swiss companies that are affiliated with financial entities in the EU and provide intra-group ICT services for their group entities in the EU also fall under the scope of DORA with these services. DORA applies to Swiss ICT service providers as soon as they intend to provide their services to corresponding financial entities in the EU.
In addition to other requirements, companies affected by DORA must carry out regular penetration tests to strengthen their digital operational resilience as well as provide corresponding evidence. These are described in EU Regulation 2022/2554 in Articles 24 to 27. In summary, there are two types of tests:
- Testing of ICT tools and systems: Testing of digital operational resilience, including by means of baseline tests, penetration tests, vulnerability scans and source code analyses.
- These are relevant for the entire financial sector.
- They must be carried out at least once a year.
- All ICT systems and applications that support critical or important functions must be tested.
- Micro-enterprises (fewer than 10 employees and less than 10 million EUR in turnover) are exempt.
- Extended tests based on TLPT: Threat-Led Penetration Tests (TLPT) and advanced tests aligned with TIBER-EU:
- TLPT only need to be performed on systemically important financial institutions with a high level of ICT maturity. Systemically important organizations are specifically named by the responsible supervisory authorities (e.g. BaFin).
- The tests must be performed at least every 3 years. All critical systems in production must be tested.
- Involved services from third-party ICT service providers must also be included in the tests.
- The results must be certified by the responsible authority.
Threat-Led Penetration Testing (TLPT) in Accordance with DORA
TLPT are threat-oriented penetration tests, similar to red teaming. In TLPT, a Thread Intelligence Provider (TIP) is used to define an attack scenario in advance based on the current threat landscape, and an attempt is made to simulate this attack in the productive system landscape. Traditional red teaming, on the other hand, attempts to achieve a goal defined by the customer or by both parties without having a path, means, or vulnerabilities predefined. However, both include a certain framework, tactics, techniques and procedures of real attackers that are perceived as a real cyber threat. These are then replicated and executed as a controlled, tailored, intelligence-led test on the financial entity’s critical live production systems.
In addition to other required regular (automated) tests, such tests must be carried out in accordance with Article 26 for the defined financial entities (see above) at least every 3 years on all critical, productive systems. This must also include the testing of involved services from third-party ICT service providers and the results must be certified by the responsible authority.
TLPT based on DORA builds heavily on the TIBER framework, but has additional legal requirements. However, the operational differences are minor.
Further information from BaFin (DE) on DORA: DORA – Digital Operational Resilience Act
Testing of ICT Tools and Systems and TLPT by Oneconsult
Oneconsult can support you as an independent service provider in the compliant implementation of DORA. Whether it be with regular security checks such as vulnerability scans, source code analyses, penetration tests and red team assessments, or Threat-Led Penetration Testing (TLPT). The reports are structured according to proven methods from many years of experience and the requirements of DORA. This also supports the voluntary exchange of information and findings between financial entities to improve “situational awareness”, as described in Art. 45.
TLPT Procedure in Germany
The responsible financial supervisory authority determines which financial entities must conduct a TLPT and sets the frequency of the tests. In order to verify that the digital operational resilience objectives of DORA are being met, Threat-Led Penetration Tests (TLPTs) must be conducted under supervision and with transparent communication of results. The added value of these TLPTs lies in the consideration and inclusion of the affected processes, people and operational IT security controls. Based on a specific threat, all lines of defense are tested – from the outer perimeter to the core assets. The process is divided into the three phases of preparation, testing and finalization:
- In the preparation phase, an attack scenario is created and defined based on the company-specific threat information. Depending on the systems affected, other service providers may also need to be involved.
- During the testing phase, technical and procedural support is provided by the TLPT Cyber Team of the supervisory authority and the customer’s own assessor. This team also maintains contact with external bodies and ultimately checks and confirms that the test has been conducted in accordance with the rules.
- The testers carry out the controlled attacks according to the defined scenario, which is not known to the Blue Team (defenders/SOC/CSIRT). The tactics, techniques and procedures of malicious attackers are used, taking into account the company-specific threat information.
- The Control Team (on the customer side) appoints the Control Manager, who acts as the contact person and decision-maker for the client. They ensure monitoring and risk management during the tests.
- In the finalization phase, the reports are prepared, the results are analyzed, and specific measures are defined to remediate the identified vulnerabilities. It also ensured that the report is submitted transparently and in full to the supervisory authority and other defined partners*.
*DORA Art. 45 regulates the voluntary exchange (within trusted networks of financial entities) of information and intelligence on cyber threats to financial entities.
This procedure was published by BaFin in December 2023 and also shows that the test methodology provides for the involvement of various stakeholders:
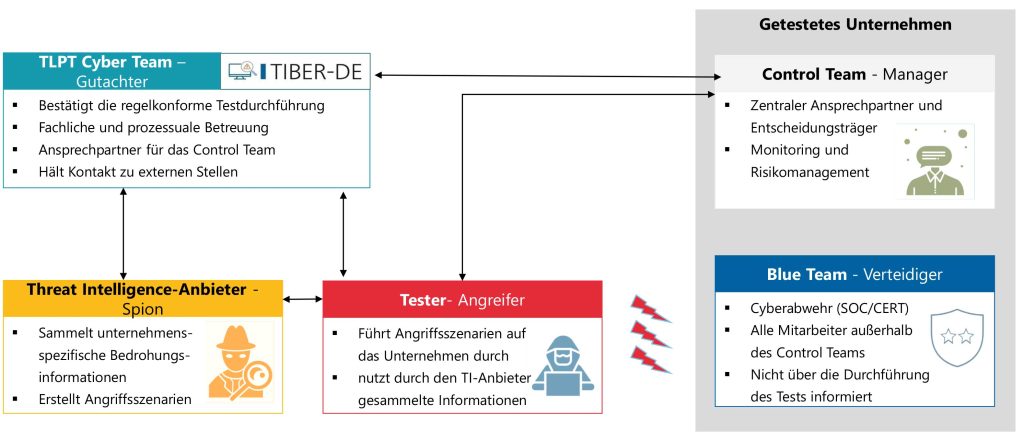
Source: Presentation of the event on 05.12.2023 “IT supervision in the financial sector” – Praesentation4_TLTP_unter_DORA, p. 8.
Oneconsult is looking forward to carrying out TLPTs and to accompanying and supporting you in this process.
Does Oneconsult Fulfill the Requirements for TLPT According to DORA?
Penetration testing and red teaming, and therefore also TLPT, have been our core competencies for 20 years. All our testers are certified and subject to appropriate ethical codes of conduct. Oneconsult has proven its technical and organizational capabilities in countless projects, especially in the financial and other critical sectors. Our guidelines for technical and organizational measures describe how Oneconsult ensures that the security of confidential data is and remains guaranteed. We also have the necessary risk insurance against misconduct and negligence. The public consultation on the Regulatory Technical Standard (RTS) of the EU supervisory authorities was concluded in March 2024. This may result in adjustments to the previously known requirements for accredited testers, which are expected to be made public in mid-July. Oneconsult currently meets all known requirements, in particular those of Art. 27 and will have this confirmed by the appropriate accreditation body as soon as it is defined by the supervisory authority.
Oneconsult fulfils all currently known requirements for external testers, in particular those of Art. 27. There will be no accreditation body according to Art. 27 1c for the certification of testers, at least not in Germany.
Further Support From Oneconsult
In addition, our Consulting Team can also provide advice and support on other topics related to digital operational resilience / DORA, such as information exchange, reporting obligations, risk management and risk identification. We can also support you with our high level of expertise and extensive experience in the following areas:
- Establishing, optimizing and supporting ICT risk management (Art. 5 to 16)
- Designing technical requirements (Art. 5 to 16)
- Setting up, checking and testing incident reporting systems (Art. 17 to 23)
Conclusion
Affected financial entities that have taken cyber resilience seriously to date and have implemented previous BaFin requirements (BAIT, KAIT, VAIT, ZAIT) and established them in their processes will also be able to quickly implement the requirements from DORA. In this case, the concretization and planning of the tests can be started. However, if this is not the case, it is advisable to call in expert and experienced support when implementing the requirements from DORA in order to create a good basis for fulfilling the requirements from DORA as quickly as possible. Oneconsult’s service portfolio provides you with ideal support in this regard, be it in carrying out tests or providing support with ICT risk management, setting up an incident reporting system as well as other requirements.
To discuss specific projects related to DORA or for further questions, please get in touch with your contact at Oneconsult or info@oneconsult.com. We look forward to hearing from you.




