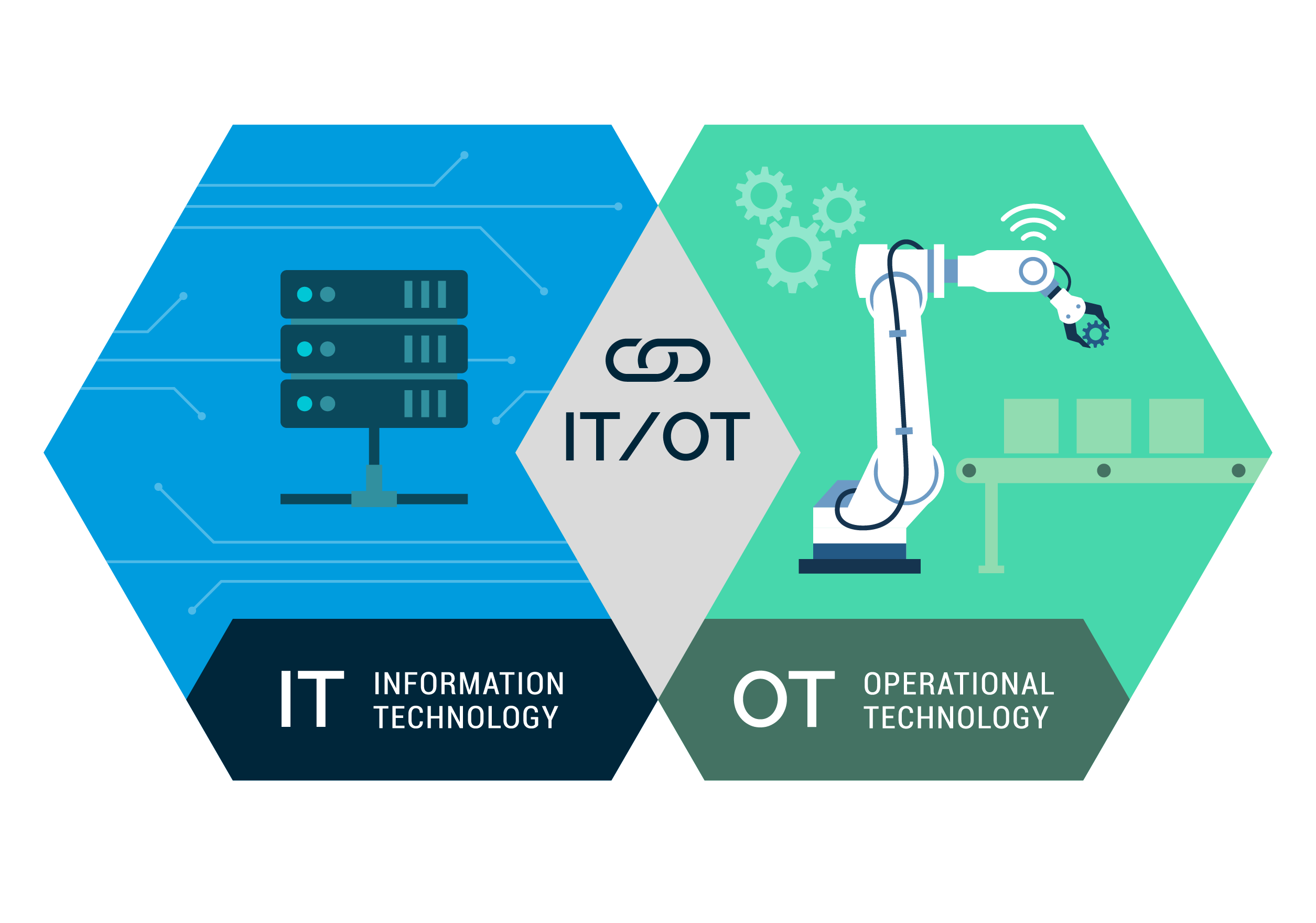
Distinction between Operational Technology and Information Technology
What would you expect power plants, production facilities and transportation companies to have in common? They all use Operational Technology (OT) in sometimes highly critical infrastructures to control industrial systems. Examples include production lines, robot systems and machines, to name just a few.