
Vulnerability Scanners and How to Protect Your Company From and With Them
Vulnerability scanners are often used during security audits. The goal: to be one step ahead of the cybercriminals!
Browse through exciting articles, current news and helpful tips & tricks from our experts on all aspects of cybersecurity.

Vulnerability scanners are often used during security audits. The goal: to be one step ahead of the cybercriminals!

A bug bounty program and a penetration test are both important measures to improve the security level of a system. However, there are important differentiators between the two that need to be understood before deciding which one to use.

Learn about the most common initial attack vectors and their protection recommendations.

Emails are a Popular Entry Point for Attackers

Configuration of a local Windows firewall and what and how it can protect against.

Do you like listening to podcasts? Get to know the best five cyber security podcasts.

PDF (Portable Document Format) files are used on a daily basis both in the working world and by private individuals. This also makes them a popular tool for cybercriminals to use in phishing attacks. They allow direct execution of scripts that can reload additional malware.
Penetration test and red teaming are cybersecurity terms. But what exactly is red teaming? And what is a penetration test all about? What are the differences between the two terms?
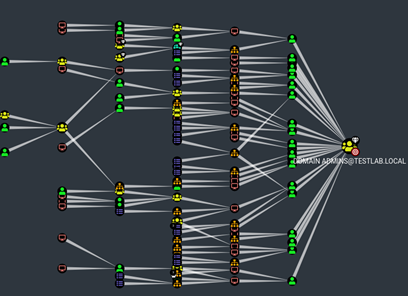
A modern Active Directory environment consists of many different components. There are clients, servers, databases, users, applications and much more. It is easy to lose track of everything (especially as a Red Team). The BloodHound tool can help here.

Computers often have strange behavior that cannot always be explained right away. Just because a laptop worked flawlessly the night before does not mean that problems won’t pop up out of nowhere the next day. In most cases, these are minor problems that can be solved quickly. However, it can also happen that the computer suddenly does not boot up at all and hangs during startup.

What are the most common security vulnerabilities in web applications? What does an attacker need to do to find and exploit them? And how can developers protect their web applications against them? Answers to these questions as well as practical hands-on examples are provided by PortSwigger’s Web Security Academy.

Ransomware has long been on everyone’s mind and part of daily news coverage. Oneconsult’s Digital Forensics and Incident Response specialists are regularly asked to present background information on such cyber attacks, discuss them and address the current threat situation. A central element is to show that all industries, company sizes and private individuals are affected by ransomware attacks and the associated risks.

From time to time, ships are blown off course, wrecked or, in the worst case, sink together with their cargo. The same can happen to the data that is sent over the Internet every day: It can deviate from its usual route and reach its destination in a big detour, but it can also end up with the wrong recipient altogether and thus be lost to the actual target – usually unintentionally, but in some cases also intentionally.

Alert fatigue refers to the phenomenon of cyber analysts being overloaded by the high number of alerts issued by security tools. This can lead to analysts overlooking or even ignoring alerts that indicate real attacks in the flood of false positives. This puts the security of the company in question at risk. Find out what the exact risks are and what measures you can take against them here.

Black Friday and Cyber Monday are not only popular with shoppers, but also with fraudsters. Here are 10 tips on how to protect yourself from such scams.

The main goal of Transport Layer Security (TLS) is to ensure confidentiality and integrity of communication channels. To meet this goal, servers should always be configured so that only cryptographic blocks recognized as “secure” can be used for TLS connections.

Is your company protected against cyberattacks? Have you implemented protective measures, but can’t determine exactly whether they are sufficient and also achieve the desired effect, or where there may still be a need?

IoTGoat is intentionally vulnerable software, like that found on routers for example.

Data leaks – incidents where unauthorized people have gained access to data collections – happen again and again. To prevent user passwords from being compromised in such a case, it is important that they are not simply stored in plain text. Instead, they should always be stored only “hashed”. This article explains which hash functions are suitable for this purpose.

Hardening IT systems is an important topic in cybersecurity. Many companies that are new to it are confronted with security incidents. Oneconsult’s Incident Response Team is dedicated to helping organizations manage such incidents.

Unwanted emails, SMS and other digital messages, also known as “spam”, are tiresome and unpleasant but also part of our everyday digital life. Nowadays, we all regularly receive unwanted messages (spam) that are not just advertising, but deliberately try to trick us into an action that can have far-reaching consequences.
Never miss the latest news about cybersecurity topics again? Subscribe to our Newsletter.
Don’t miss anything! Subscribe to our free newsletter.
Availability Monday to Friday 8:00 a.m. – 6:00 p.m (exception: customers with SLA – please call the 24/7 IRR emergency number).
Private individuals please contact your trusted IT service provider or the local police station.
For more information about our DFIR services here:
