Using realistic attack simulations, we put your security measures to the test. We show you how well your defense mechanisms can actually withstand a malicious attacker in practice – and where they cannot. For the vulnerabilities identified, we provide you with targeted measures for improvement and, if required, support you in implementing them.
A chain is only as strong as its weakest link. Close vulnerabilities before they are exploited. We help you secure your infrastructure against cyberthreats, both physically and digitally.
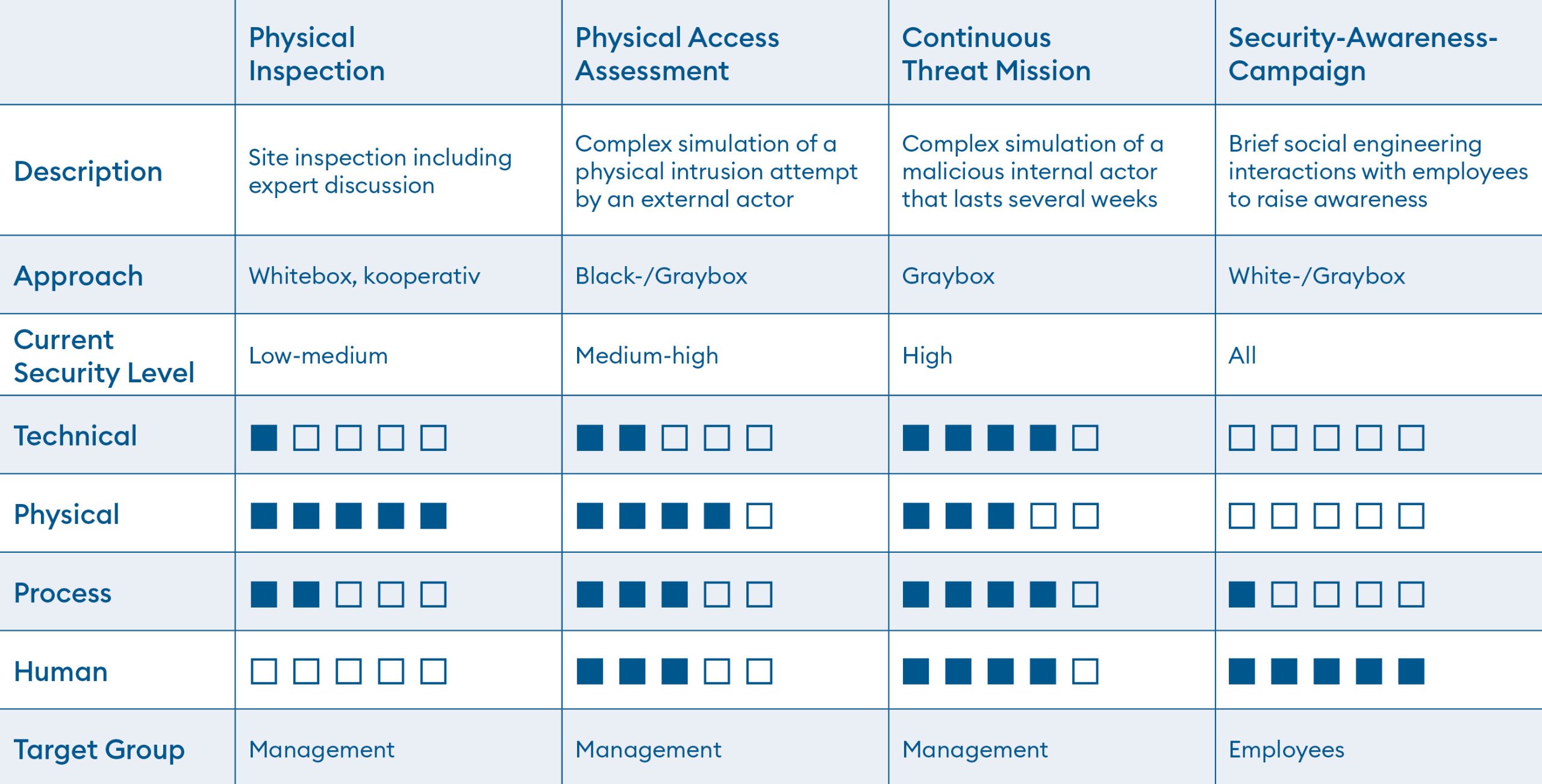
Integrated security is based on mitigating digital, physical, process, and human risks. That’s why we attack not only in cyberspace, but also physically on site using social engineering. We test your existing defense measures holistically to find even the very last security gaps.
We test your security measures from the perspective of an internal or external threat actor – tailored to meet your specific needs. Our simulations can also model advanced persistent threats (APT) or incorporate techniques from the MITRE ATT&CK® or TIBER framework.
Once the tests have been completed, you will receive a final report tailored to the target group and including a management summary. We provide a detailed description of all vulnerabilities in your security measures and systematically assess the associated risks. We recommend practical measures to mitigate the risks identified, along with an estimate of the effort required.
Our highly specialized Attack Simulation Team brings together the experience of experts from a wide range of fields, including cybersecurity, application development, justice, forensics, law enforcement, military counterespionage and countersabotage, crisis communication, etc.
In addition to extensive training and continuing education, our experts hold various widely recognized cybersecurity certifications such as CRTO, CRTL, GXPN, BSCP, OSCP, OSCE, OSWE, and others.
We regularly identify vulnerabilities in the security measures of even high-level customers with a highly hardened infrastructure, for example, by gaining access to highly privileged accounts and sensitive areas, thereby bypassing established security measures.
Contact us today – we will help you to strengthen your security strategy with our Attack Simulation services!
Although penetration testing and attack simulations both identify vulnerabilities in IT systems, they differ in their approach. Attack simulations use continuous and repetitive techniques to test an organization’s defense strategies on an ongoing basis. Penetration testing, on the other hand, is a targeted, one-time test within a specified timeframe. The continuous approach of attack simulations makes them particularly valuable given the dynamic threat landscape.
Attack simulations are crucial for identifying security gaps at an early stage and responding to new threats. Ideally, they should be performed on an ongoing basis, or at least quarterly, to keep security measures up to date.
Availability Monday to Friday 8:00 a.m. – 6:00 p.m (exception: customers with SLA – please call the 24/7 IRR emergency number).
Private individuals please contact your trusted IT service provider or the local police station.
For more information about our DFIR services here:

Don’t miss anything! Subscribe to our free newsletter.