Home | Services | Attack Simulation | Red Teaming
We take a holistic approach that allows us to see the big picture and uncover security gaps in the interactions and interfaces between different systems in your infrastructure. Traditional security checks on individual systems can easily miss such vulnerabilities.
We conduct realistic cyberattacks to test how your systems and employees respond to real threats. Test your security measures against current and common threats, which include known advanced persistent threats (APTs) for example.
Our red team tests not only your IT systems, but also the effectiveness of your security processes – because only through a strong interplay between these two elements can a secure organization be achieved.
Our professional red teaming simulations demonstrate to your customers and partners that cybersecurity is a top priority in your organization and that you are continuously improving.
Our highly qualified experts test your level of security from the perspective of a real attacker. The final report details how existing vulnerabilities can be exploited, allowing you to refine your defensive strategies in a targeted manner.
We simulate a complete attack cycle as it would occur in reality:
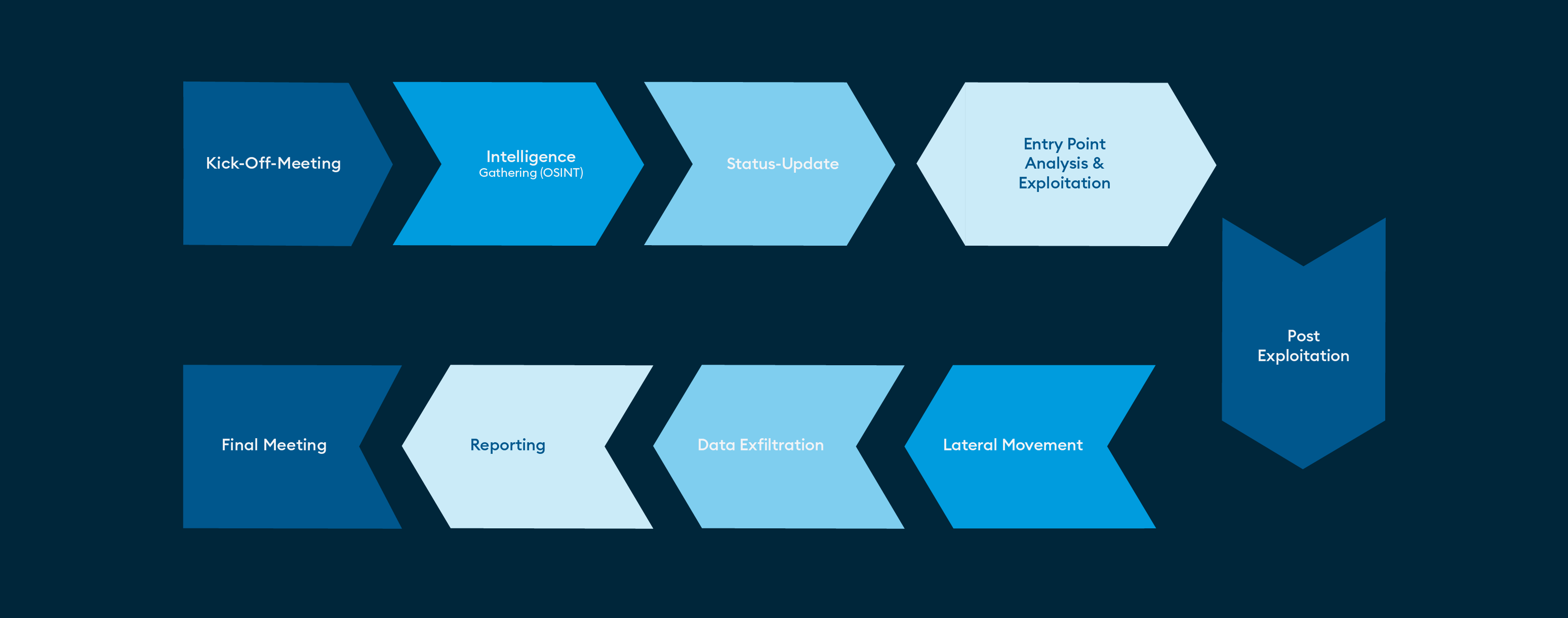
Our Red Teaming service proactively prepares your organization for cyberthreats. Our experts work closely with you to develop customized attack scenarios that meet your unique needs and risk profile.
Our experienced specialists detect vulnerabilities in your systems and processes and provide valuable insights and recommendations for continuous improvement of your security measures.
Enhance your security strategy with our powerful Red Teaming service to effectively identify and defend against potential threats.
Contact us – we will be happy to discuss your needs individually!
Red teaming is suitable for all companies and institutions that already have basic security measures in place. Red teaming allows you to test both a (seemingly) proven defense system and the correct implementation of new measures. For more details see our blog post: “Red Teaming: What Are the Benefits and Who Is It Useful For?”
Both types of tests have similar goals, but different approaches. Penetration testing focuses on identifying vulnerabilities and security gaps in a specific environment. Red teaming, on the other hand, goes one step further and simulates a comprehensive attack on an organization’s systems to test its resilience to real-world cyberthreats in a hands-on way. More information can be found in our blog post: “The Differences Between Penetration Test and Red Teaming”
Red teaming enables a comprehensive and interlinked assessment of security measures by testing an organization’s defense mechanisms in a realistic scenario. This helps organizations identify and eliminate vulnerabilities and improve their defensive measures. Red teaming also fosters a better understanding of risks and supports the development of a proactive security culture.
Availability Monday to Friday 8:00 a.m. – 6:00 p.m (exception: customers with SLA – please call the 24/7 IRR emergency number).
Private individuals please contact your trusted IT service provider or the local police station.
For more information about our DFIR services here:

Don’t miss anything! Subscribe to our free newsletter.